Examples of policy summaries
The following examples include JSON policies with their associated policy summaries, the service summaries, and the action summaries to help you understand the permissions given through a policy.
Policy 1: DenyCustomerBucket
This policy demonstrates an allow and a deny for the same service.
DenyCustomerBucket Policy Summary:

DenyCustomerBucket S3 (Explicit deny) Service Summary:

GetObject (Read) Action Summary:

Policy 2: DynamoDbRowCognitoID
This policy provides row-level access to Amazon DynamoDB based on the user's Amazon Cognito ID.
DynamoDbRowCognitoID Policy Summary:

DynamoDbRowCognitoID DynamoDB (Allow) Service Summary:

GetItem (List) Action Summary:

Policy 3: MultipleResourceCondition
This policy includes multiple resources and conditions.
MultipleResourceCondition Policy Summary:
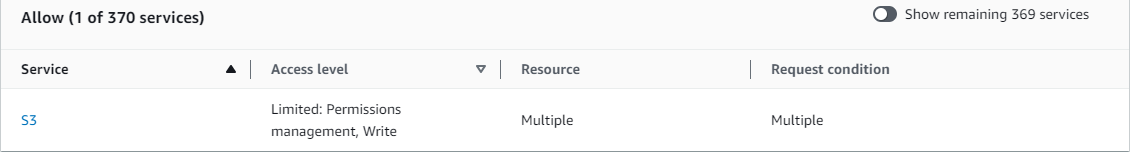
MultipleResourceCondition S3 (Allow) Service Summary:

PutObject (Write) Action Summary:

Policy 4: EC2_troubleshoot
The following policy allows users to get a screenshot of a running Amazon EC2 instance, which can help with EC2 troubleshooting. This policy also permits viewing information about the items in the Amazon S3 developer bucket.
EC2_Troubleshoot Policy Summary:

EC2_Troubleshoot S3 (Allow) Service Summary:

ListBucket (List) Action Summary:

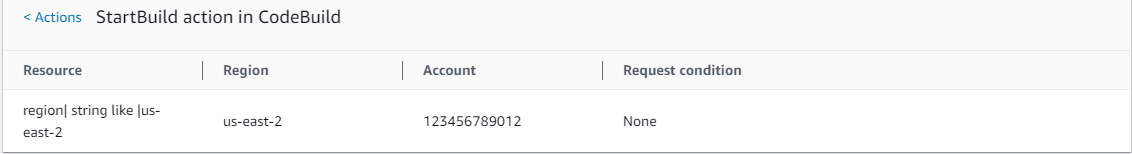
Policy 5: CodeBuild_CodeCommit_CodeDeploy
This policy provides access to specific CodeBuild, CodeCommit, and CodeDeploy resources. Because these
resources are specific to each service, they appear only with the matching service. If you
include a resource that does not match any services in the Action element, then
the resource appears in all action summaries.
CodeBuild_CodeCommit_CodeDeploy Policy Summary:

CodeBuild_CodeCommit_CodeDeploy CodeBuild (Allow) Service Summary:

CodeBuild_CodeCommit_CodeDeploy StartBuild (Write) Action Summary: