Las traducciones son generadas a través de traducción automática. En caso de conflicto entre la traducción y la version original de inglés, prevalecerá la version en inglés.
Configuración del agente de AWS AppConfig para recuperar las configuraciones de varias cuentas
Puede configurar el AWS AppConfig agente para que recupere configuraciones de varios archivos Cuentas de AWS introduciendo las anulaciones de credenciales en el manifiesto del AWS AppConfig agente. Las anulaciones de credenciales incluyen el nombre de recurso de Amazon (ARN) de una función AWS Identity and Access Management (IAM), un ID de función, un nombre de sesión y la duración del tiempo que el agente puede asumir la función.
Introduzca estos detalles en la sección de credenciales del manifiesto. La sección de credenciales utiliza el siguiente formato:
{ "application_name:environment_name:configuration_name": { "credentials": { "roleArn": "arn:partition:iam::account_ID:role/roleName", "roleExternalId": "string", "roleSessionName": "string", "credentialsDuration": "time_in_hours" } } }
A continuación se muestra un ejemplo:
{ "My2ndApp:Beta:MyEnableMobilePaymentsFeatureFlagConfiguration": { "credentials": { "roleArn": "arn:us-west-1:iam::123456789012:role/MyTestRole", "roleExternalId": "00b148e2-4ea4-46a1-ab0f-c422b54d0aac", "roleSessionName": "AWSAppConfigAgent", "credentialsDuration": "2h" } } }
Antes de recuperar una configuración, el agente lee los detalles de las credenciales de la configuración del manifiesto y, a continuación, asume el rol de IAM especificado para esa configuración. Puede especificar un conjunto diferente de anulaciones de credenciales para diferentes configuraciones en un solo manifiesto. En el siguiente diagrama, se muestra cómo el AWS AppConfig agente, mientras se ejecuta en la cuenta A (la cuenta de recuperación), asume funciones distintas especificadas para las cuentas B y C (las cuentas del proveedor) y, a continuación, llama a la operación de la GetLatestConfigurationAPI para recuperar los datos de AWS AppConfig configuración que se ejecutan en esas cuentas:
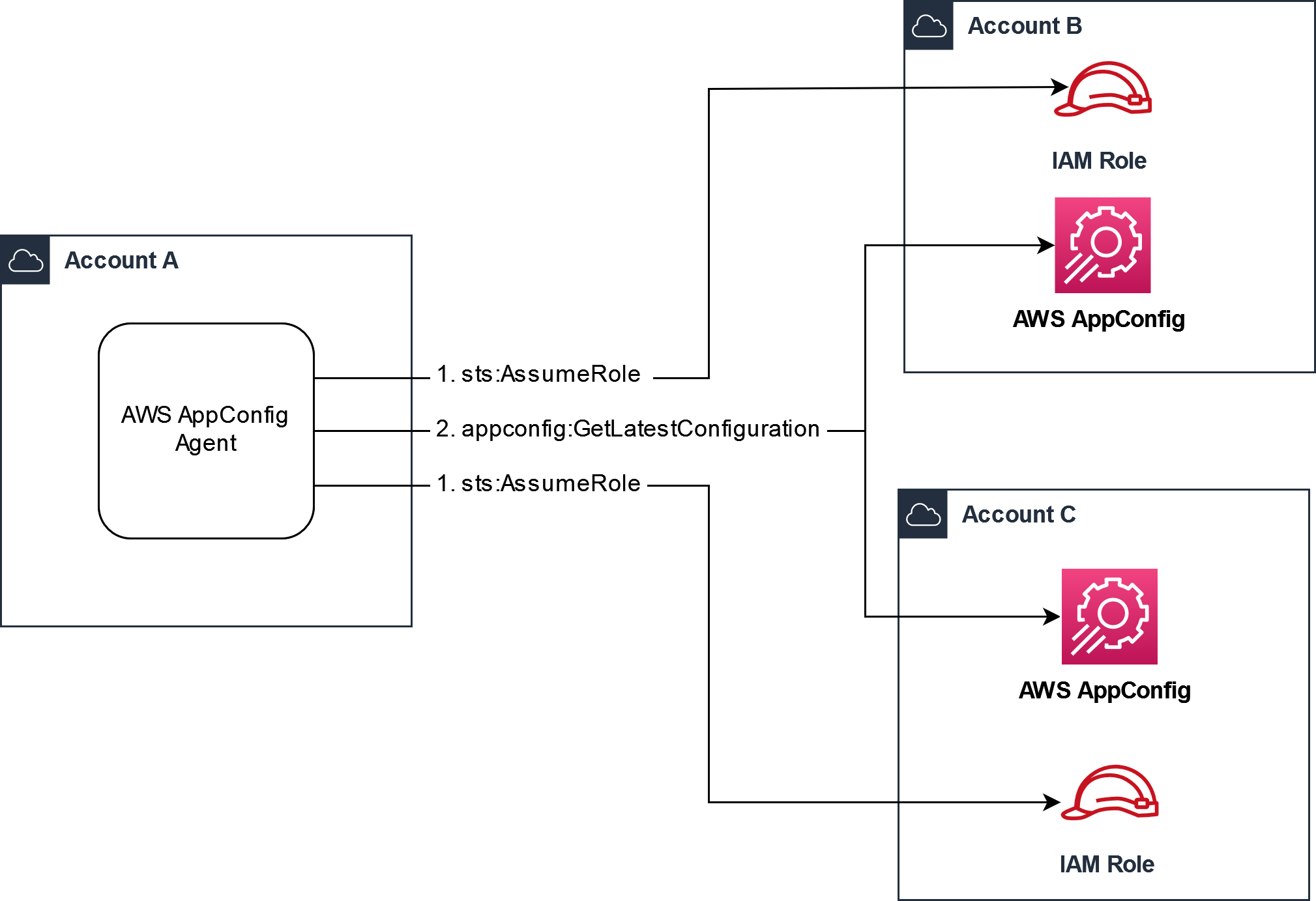
Configuración de permisos para recuperar los datos de configuración de cuentas de proveedor
AWS AppConfig El agente que se ejecuta en la cuenta de recuperación necesita permiso para recuperar los datos de configuración de las cuentas del proveedor. Para conceder el permiso al agente, debe crear un rol AWS Identity and Access Management (IAM) en cada una de las cuentas de los proveedores. AWS AppConfig El agente de la cuenta de recuperación asume esta función para obtener datos de las cuentas de los proveedores. Complete los procedimientos de esta sección para crear una política de permisos de IAM, un rol de IAM y agregar anulaciones de agente al manifiesto.
Antes de empezar
Recopile la siguiente información antes de crear una política de permisos y un rol en IAM.
-
El IDs para cada uno Cuenta de AWS. La cuenta de recuperación es la cuenta que llamará a otras cuentas para obtener datos de configuración. Las cuentas de proveedor son las cuentas que venderán datos de configuración a la cuenta de recuperación.
-
El nombre de la función de IAM utilizada AWS AppConfig en la cuenta de recuperación. Esta es una lista de las funciones que utilizan AWS AppConfig, de forma predeterminada:
-
Para Amazon Elastic Compute Cloud (Amazon EC2), AWS AppConfig usa el rol de instancia.
-
Para AWS Lambda, AWS AppConfig utiliza la función de ejecución Lambda.
-
Para Amazon Elastic Container Service (Amazon ECS) y Amazon Elastic Kubernetes Service (Amazon AWS AppConfig EKS), utiliza la función de contenedor.
Si ha configurado el AWS AppConfig agente para que utilice un rol de IAM diferente especificando la variable de
ROLE_ARNentorno, anote ese nombre. -
Creación de la política de permisos
Utilice el siguiente procedimiento para crear una política de permisos mediante la consola de IAM. Complete el procedimiento de cada uno Cuenta de AWS de ellos para enviar los datos de configuración de la cuenta de recuperación.
Para crear una política de IAM
-
Inicie sesión AWS Management Console en una cuenta de proveedor.
Abra la consola de IAM en https://console.aws.amazon.com/iam/
. -
En el panel de navegación, seleccione Políticas y, a continuación, Crear política.
-
Elija la opción JSON.
-
Elija Editor de políticas y sustituya el JSON predeterminado por la siguiente instrucción de política. Actualiza cada una
example resource placeholdercon los detalles de la cuenta del proveedor.{ "Version": "2012-10-17", "Statement": [{ "Effect": "Allow", "Action": [ "appconfig:StartConfigurationSession", "appconfig:GetLatestConfiguration" ], "Resource": "arn:partition:appconfig:region:vendor_account_ID:application/vendor_application_ID/environment/vendor_environment_ID/configuration/vendor_configuration_ID" } ] }A continuación se muestra un ejemplo:
{ "Version": "2012-10-17", "Statement": [{ "Effect": "Allow", "Action": [ "appconfig:StartConfigurationSession", "appconfig:GetLatestConfiguration" ], "Resource": "arn:aws:appconfig:us-east-2:111122223333:application/abc123/environment/def456/configuration/hij789" } ] } -
Elija Next (Siguiente).
-
En el campo Nombre de la política escriba un nombre.
-
(Opcional) En Agregar etiquetas, agregue uno o varios pares de valor etiqueta-clave para organizar, realizar un seguimiento o controlar el acceso a esta política.
-
Elija Crear política. El sistema le devuelve a la página Policies (Políticas).
-
Repita este procedimiento en cada una de las Cuenta de AWS que vendan los datos de configuración de la cuenta de recuperación.
Creación del rol de IAM
Utilice el siguiente procedimiento para crear un rol de IAM mediante la consola de IAM. Complete el procedimiento de cada una de ellas para Cuenta de AWS vender los datos de configuración de la cuenta de recuperación.
Cómo crear un rol de IAM
-
Inicie sesión AWS Management Console en una cuenta de proveedor.
Abra la consola de IAM en https://console.aws.amazon.com/iam/
. -
En el panel de navegación, seleccione Roles y luego seleccione Crear política.
-
En Tipo de entidad de confianza, elija Cuenta de AWS.
-
En la sección Cuenta de AWS, elija Otra Cuenta de AWS.
-
En el campo ID de cuenta, introduzca el ID de la cuenta de recuperación.
-
(Opcional) Como práctica recomendada de seguridad para este supuesto rol, seleccione Requerir ID externo e introduzca una cadena.
-
Elija Next (Siguiente).
-
En la página Agregar permisos, utilice el campo Buscar para localizar la política que creó en el procedimiento anterior. Seleccione la casilla de verificación situada junto a su nombre.
-
Elija Next (Siguiente).
-
En Role name (Nombre de rol), escriba un nombre.
-
(Opcional) En Description (Descripción), introduzca una descripción.
-
En Paso 1: seleccionar entidades de confianza, elija Editar. Reemplace la política de confianza JSON predeterminada por la siguiente política. Actualiza cada una
example resource placeholdercon la información de tu cuenta de recuperación.{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::retrieval_account_ID:role/appconfig_role_in_retrieval_account" }, "Action": "sts:AssumeRole" } ] } -
(Opcional) En Tags (Etiquetas), agregue uno o varios pares de valor etiqueta-clave para organizar, realizar un seguimiento o controlar el acceso a este rol.
-
Elija Create role. El sistema le devuelve a la página Roles.
-
Busque el rol que acaba de crear. Elíjalo. En la sección ARN, copie el ARN. Especificará esta información en el siguiente procedimiento.
Agregación de anulaciones de credenciales al manifiesto
Tras crear el rol de IAM en su cuenta de proveedor, actualice el manifiesto en la cuenta de recuperación. En concreto, agregue el bloque de credenciales y el ARN del rol de IAM para recuperar los datos de configuración de la cuenta de proveedor. Este es el formato JSON:
{ "vendor_application_name:vendor_environment_name:vendor_configuration_name": { "credentials": { "roleArn": "arn:partition:iam::vendor_account_ID:role/name_of_role_created_in_vendor_account", "roleExternalId": "string", "roleSessionName": "string", "credentialsDuration": "time_in_hours" } } }
A continuación se muestra un ejemplo:
{ "My2ndApp:Beta:MyEnableMobilePaymentsFeatureFlagConfiguration": { "credentials": { "roleArn": "arn:us-west-1:iam::123456789012:role/MyTestRole", "roleExternalId": "00b148e2-4ea4-46a1-ab0f-c422b54d0aac", "roleSessionName": "AwsAppConfigAgent", "credentialsDuration": "2h" } } }
Cómo validar que la recuperación de varias cuentas esté funcionando
Puede comprobar que ese agente puede recuperar los datos de configuración de varias cuentas consultando los registros del AWS AppConfig agente. El registro de nivel INFO de los datos iniciales recuperados de “YourApplicationName:YourEnvironmentName:YourConfigurationName” es el mejor indicador de que las recuperaciones se han realizado correctamente. Si las recuperaciones fallan, debería ver un registro de nivel ERROR que indique el motivo del error. A continuación, se muestra un ejemplo de una recuperación de una cuenta de proveedor realizada correctamente:
[appconfig agent] 2023/11/13 11:33:27 INFO AppConfig Agent 2.0.x [appconfig agent] 2023/11/13 11:33:28 INFO serving on localhost:2772 [appconfig agent] 2023/11/13 11:33:28 INFO retrieved initial data for 'MyTestApplication:MyTestEnvironment:MyDenyListConfiguration' in XX.Xms