Connecting to RISE from your AWS account
You can connect to RISE from your AWS account in the following ways.
Topics
Amazon VPC peering
VPC peering enables network connection between two AWS VPCs using private IPv4 and IPv6 addresses. Instances can communicate over the same network. For more information, see What is VPC peering?
Before setting up a VPC peering connection, you need to create a request for SAP's approval. For a successful VPC peering, the defined IPv4 Classless Inter-Domain Routing (CIDR) block must not overlap. Check with SAP for the CIDR ranges that can be used in RISE with SAP VPC.
VPC peering is one-on-one connection between VPCs, and is not transitive. Traffic cannot transit from one VPC to another via an intermediary VPC. You must setup multiple peering connections to establish direct communication between RISE with SAP VPC and multiple VPCs.
VPC peering works across AWS Regions. All inter-Region traffic is encrypted with no single point of failure or bandwidth bottleneck. Traffic stays on AWS Global Network and never traverses the public internet, reducing threats of common exploits and DDoS attacks.

Data transfer for VPC peering within an Availability Zone is free, and for across Availability Zones
is charged per-GB for "data in" to and "data out". Data transfer for VPC peering for across regions
is charged for "out" per-GB. For more information, see Amazon EC2 pricing
|
Pricing example - VPC peering across Availability Zones 
100GB of data sent from the AWS account – managed by SAP via VPC Peering toward the AWS account – managed by Customer across AZs: 100GB * $0.01per-GB = $1 (out - billed to AWS account – managed by SAP) and 100GB * $0.01per-GB = $1 (IN - billed to AWS account – managed by Customer) As the cost for data transfer is included In the RISE subscription, the AWS account – managed by Customer will only incur the cost for traffic IN e.g. $0.01 per-GB. [note: the cost example also applies when Sender is AWS account – managed by Customer and Receiver is AWS account – managed by SAP] |
|
Pricing example - VPC peering across Regions [note: cost between AWS Regions vary. For more information see: Amazon EC2 pricing Data Transfer 
1). 100GB of data sent from the AWS account – managed by SAP via VPC Peering toward the AWS account – managed by Customer across Regions. 100GB * ($0.01-$0.138per-GB) = $1-$13.8 (out - billed to AWS account – managed by SAP) As the cost for data transfer is included In the RISE subscription the AWS account – managed by Customer will not incur cost for this example. 2). 100GB of data sent from the AWS account – managed by Customer via VPC Peering toward the AWS account – managed by SAP across Regions. 100GB * ($0.01-$0.138per-GB) = $1-$13.8 (out - billed to AWS account – managed by Customer) As the cost for data transfer is calculated for “data out” the AWS account – managed by Customer will incur the cost for this example. |
AWS Transit Gateway
AWS Transit Gateway is a network transit hub to interconnect Amazon VPCs. It acts as a cloud router, resolving complex peering setup issues by acting as the central communication hub. You need to establish this connection with AWS account managed by SAP only once.
Transit Gateway in your own AWS account
To establish connection with AWS account managed by SAP, create and share AWS Transit Gateway via AWS Resource Access Manager (RAM) in your AWS account. SAP then creates an attachment to enable traffic flow through an entry in route table. As AWS Transit Gateway resides in your AWS account, you can retain control over traffic routing. For more information, see Transit gateway peering attachments.

Transit Gateway in AWS account managed by SAP
When you already have an Transit Gateway in another AWS Region, and cannot create another AWS account with Transit Gateway in the Region that has RISE with SAP account, then SAP can provide the Transit Gateway in the RISE with SAP account that will be managed by SAP. You can enable communication between your Transit Gateway and SAP managed Transit Gateway through Transit Gateway Peering. You cannot connect VPC attachments of VPCs outside of the RISE environment to the SAP-managed Transit Gateway.
For peering attachments, each Transit Gateway owner is billed hourly for the peering
attachment with the other Transit Gateway, thus the hourly cost for the peering attachment
of the Transit Gateway in the SAP account - managed by SAP (for the purpose of Inter Region
Transit Gateway Peering) is part of the RISE subscription. However the hourly cost for the
peering attachment of the Transit Gateway in the Customer account – Customer managed is billed
to the Customer. For more information, see:
Transit Gateway pricing
|
Pricing example - Transit Gateway across VPCs in different Regions [note: cost between AWS Regions vary. For more information see: Amazon EC2 pricing Data Transfer 
1). 100GB of data sent from a VPC in Region X in the AWS account – managed by SAP via the Transit Gateway that resided in the AWS account – managed by SAP, towards a peered Transit Gateway, in a different Region Y, that resided in the AWS account – managed by Customer ending at a VPC in the AWS account – managed by Customer: 100GB * $0.02per-GB = $2 (Transit Gateway data processing) + 100GB * ($0.01-$0.138per-GB) = $1-$13.8 (Region out) = $3-$15.8 (Total - billed to AWS account – managed by SAP) Data processing is charged to the VPC owner who sends the traffic to Transit Gateway. As the sending VPC is residing in the AWS account – managed by SAP and the cost for data transfer is included in the RISE Subscription, thus the AWS account – managed by Customer will not incur data transfer cost for this example. As data processing charges do not apply for data sent from a peering attachment to a Transit Gateway and inbound inter-Region data transfer charges are free, no further Data Transfer charges apply to the AWS account – managed by Customer. The AWS account – managed by Customer will only be billed for the price per Transit Gateway peering attachment per hour. Data out of an AZ will always go via Transit Gateway endpoint in that AZ to reach other VPC, so there is no cross AZ Data Transfer costs. 2). 100GB of data sent from a VPC in region Y in the AWS account – managed by Customer via the Transit Gateway that resided in the AWS account – managed by Customer, towards a peered Transit Gateway, in a different region X, that resided in the AWS account – managed by SAP ending at a VPC in the AWS account – managed by SAP: 100GB * $0.02per-GB = $2 (Transit Gateway data processing) + 100GB * ($0.01-$0.138per-GB) = $1-$13.8 (Region out) = $3-$15.8 (Total - billed to AWS account – managed by Customer) Data processing is charged to the VPC owner who sends the traffic to Transit Gateway. As the sending VPC is residing in the AWS account – managed by Customer all data transfer cost for this example are billed to the AWS account – managed by Customer. In addition, the AWS account – managed by Customer will be billed for the price per Transit Gateway peering attachment per hour. |
Connecting to RISE using your single AWS account
You can establish connectivity between on-premises and RISE with SAP VPC using your AWS account. This method provides you with more control but also requires managing AWS services in your AWS account. You can use any one of the following options.
-
AWS Transit Gateway – Share AWS Transit Gateway resource in you AWS account with AWS account managed by SAP.
-
AWS VPN with AWS Transit Gateway – Create an IPsec VPN connection between your remote network and transit gateway over the internet. For more information, see How AWS Site-to-Site VPN works and Transit gateway VPN attachments.
-
Direct Connect gateway – Create a Direct Connect gateway with a transit virtual interface. For more information, see Transit gateway attachments to a Direct Connect gateway.
To strengthen the security, see How do I establish an AWS VPN over an AWS Direct Connect connection?
The following image shows this option within the same AWS Region.

The following image shows this option across different AWS Regions.
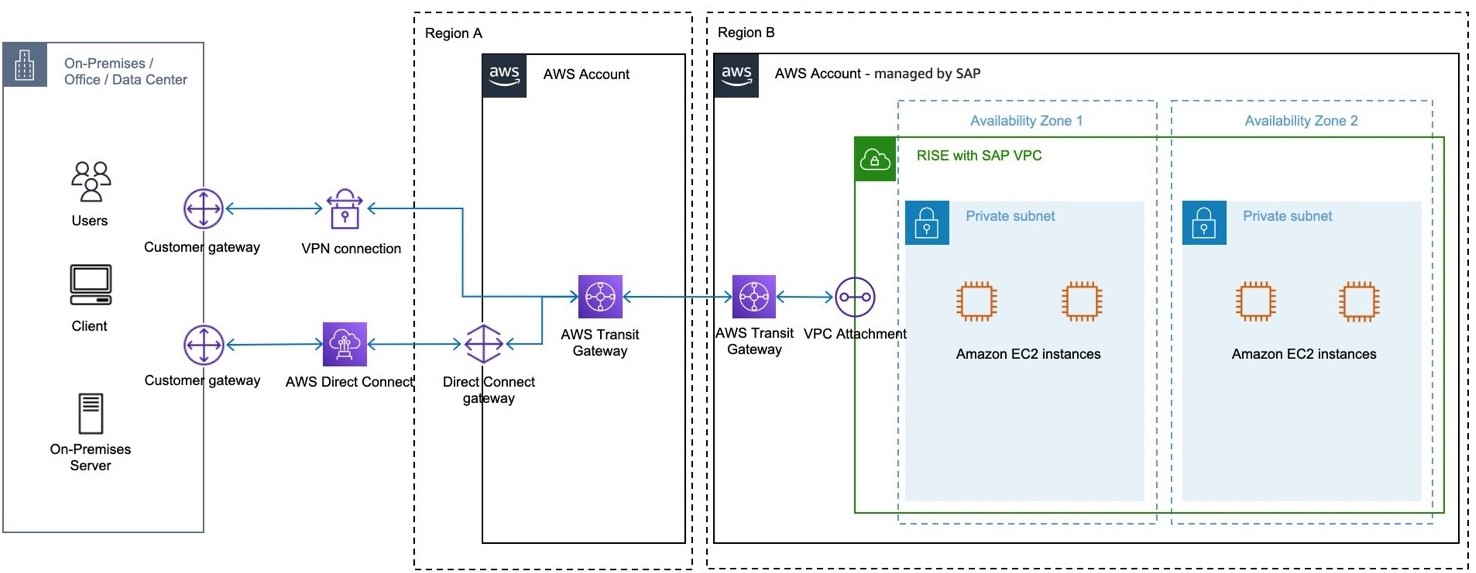
When you choose AWS Site-to-Site VPN and/or AWS Direct Connect to establish connectivity between on-premises and RISE with SAP VPC using a Transit Gateway in the AWS account - managed by the Customer, either in the same AWS Region or a different AWS Region than the RISE with SAP VPC, the following applies.
Hourly cost:
As the AWS Site-to-Site VPN is residing in the AWS account – managed by Customer and is attached to the Transit Gateway that resides in the AWS account – managed by Customer, the cost for the VPN connection and the cost for the Transit Gateway attachment are billed to the AWS account – managed by Customer
As the Direct Connect and Direct Connect Gateway is residing in the AWS account – managed by Customer and is attached to the Transit Gateway that resides in the AWS account – managed by Customer the cost for the AWS Direct Connect ports hours and the cost for the Transit Gateway attachment are billed to the AWS account – managed by Customer.
For peering attachments, each Transit Gateway owner is billed hourly for the peering attachment with the other Transit Gateway.
Data processing charges:
Data processing charges apply for each gigabyte sent from a VPC, Direct Connect or VPN to/via the Transit Gateway.
Depending on the source and destination the data processing charges vary and will be billed to the AWS account – managed by Customer, or are already included in the RISE subscription (For a cost estimation example: see below)
For more information see:
|
Pricing example – Transit Gateway in VPCs in the same region via VPN or Direct Connect [note: cost between AWS Regions vary. For more information see: Amazon EC2 pricing Data Transfer 
1). 200GB of data sent from a VPC in the AWS account – managed by SAP via the Transit Gateway that resided in the AWS account – managed by Customer via a VPN or Direct Connect in the AWS account – managed by SAP towards On-Premises: 200GB * $0.02per-GB = $4 (Transit Gateway data processing) + 100 GB * $0.09per-GB = $9 (VPN data transfer out, with the first 100 GB are free, then $ 0.09 per-GB) = $13 (Total data transfer out billed to AWS account – managed by SAP) or 200GB * $0.02per-GB = $4 (Transit Gateway data processing) + 200GB * ($0.02-$0.19per-GB) = $4-$38 (Direct Connect data transfer out) = $8-$42 (Total data transfer out billed to AWS account – managed by SAP) Data processing is charged to the VPC owner who sends the traffic to Transit Gateway. As the sending VPC is residing in the AWS account – managed by SAP and the cost for data transfer is included in the RISE Subscription, therefore the AWS account – managed by Customer will not incur Data Transfer cost in this example. 2). 200GB of data sent from On-Premises via a VPN or Direct Connect in the AWS account – managed by Customer via the Transit Gateway that resided in the AWS account – managed by Customer towards VPC in the AWS account – managed by SAP: 200GB * $0.00per-GB = $0 (VPN data transfer in) + 200GB * $0.02per-GB = $4 (Transit Gateway data processing) + $0 (VPN data transfer in) = $4 (Total data transfer in billed to AWS account – managed by Customer) or 200GB * $0.00per-GB = $0 (Direct Connect data transfer in) + 200GB * $0.02per-GB = $4 (Transit Gateway data processing) = $4 (Total data transfer in billed to AWS account – managed by Customer) Data transfer into AWS is free and this also applies to VPN and Direct Connect therefore the only data processing charge is the data processing of the Transit Gateway. As Transit Gateway resides in the AWS account – managed by Customer the cost for data transfer is billed to the AWS account – managed by Customer |
|
Pricing example – Transit Gateway in VPCs in the different regions via VPN or Direct Connect [note: cost between AWS Regions vary. For more information see: Amazon EC2 pricing Data Transfer 
1). 200GB of data sent from a VPC in the AWS account – managed by SAP via the Transit Gateway that resided in the AWS account – managed by SAP that is peered with an Transit Gateway in a different Region in the AWS account – managed by Customer via a VPN OR Direct Connect in the AWS account – managed by Customer towards On-Premises: 200GB * $0.02per-GB = $4 (Transit Gateway data processing) + 200GB * ($0.01-$0.138per-GB) = $2-$27.6 (Region out) + 100GB * $0.09per-GB = $9 (VPN data transfer out, with the first 100 GB are free, then $ 0.09 per-GB) = $15-$40.6 (Total data transfer out billed to AWS account – managed by SAP) or 200GB * $0.02per-GB = $4 (Transit Gateway data processing) + 200GB * ($0.01-$0.138per-GB) = $2-$27.6 (Region out) + 200GB * ($0.02-$0.19per-GB) = $4-$38 (Direct Connect data transfer out) = $10-$69.6 (Total data transfer out billed to AWS account – managed by SAP) Data processing is charged to the VPC owner who sends the traffic to Transit Gateway. As the sending VPC is residing in the AWS account – managed by SAP and the cost for Data Transfer is included in the RISE subscription, therefore the AWS account – managed by Customer will not incur Data Transfer cost in this example. 2). 200GB of data sent from On-Premises via a VPN or Direct Connect in the AWS account – managed by Customer via the Transit Gateway that resided in the AWS account – managed by Customer via a peered Transit Gateway in a different region in the AWS account – managed by SAP towards a VPC in the AWS account – managed by SAP: 200GB * $0.02per-GB = $4 (Transit Gateway data processing) + 200GB * $0.00per-GB = $0 (VPN data transfer in) + 200GB * ($0.01-$0.138per-GB) = $2-$27.6 (Region out) = $6-$31.6 (Total data transfer in billed to AWS account – managed by Customer) or 200GB * $0.02per-GB = $4 (Transit Gateway data processing) + 200GB * $0.00per-GB = $0 (Direct Connect data transfer in) + 200GB * ($0.01-$0.138per-GB) = $2-$27.6 (Region out) = $6-$31.6 (Total data transfer in billed to AWS account – managed by Customer) Data transfer into AWS in is free and this also applies to VPN and Direct Connect therefore the data processing charge is the data processing of the Transit Gateway and the inter-region data transfer charges. As Transit Gateway resides in the AWS account – managed by Customer, the cost for data transfer is billed to the AWS account – managed by Customer. |
Connecting to RISE with a shared AWS Landing Zone
Modern SAP landscapes have several connectivity requirements. Services are accessed across on-premises and AWS Cloud as well as across a variety of SaaS solutions and other cloud service providers.
Creating an AWS Landing Zone facilitates secure and scalable connectivity for RISE with SAP. It provides the following benefits:
-
Control over networking configuration
-
Ability to reuse AWS Direct Connect connections across your broader AWS solutions
-
Reduced network hops and latency for connectivity to other SaaS solutions and cloud service providers as they are not routed via on-premises
-
Ability for additional governance and control through use of AWS services
A Landing Zone is designed to help organizations achieve their cloud initiatives by
automating the set-up of an AWS environment that follows AWS Well
Architected
The key components and benefits of a Landing Zone include:
-
Multi-account structure – it sets a baseline environment across multiple AWS accounts using an organization unit (OU) structure for different workloads. For instance, production, development, shared services, etc.
-
AWS Identity and Access Management – it configures AWS Identity and Access Management
(IAM) roles and policies for secure access and management of permissions. -
Networking – it sets up a Amazon Virtual Private Cloud
(Amazon VPC) with subnets, routing tables, and security groups, following the best practices for network isolation and security. -
Logging and monitoring – it configures AWS services, such as AWS Config
, AWS CloudTrail , Amazon GuardDuty for centralized logging, monitoring, and auditing of resource changes and security events. -
Security – it implements AWS security best practices, such as like enabling AWS Config Rules, setting up AWS CloudTrail trails, and creating AWS Security Hub
standards. -
Automation – it uses AWS CloudFormation
templates and AWS Service Catalog to automate the deployment and management of the Landing Zone environment. -
Customization – it allows for customization and extension based on specific organizational requirements, such as adding additional AWS services or integrating with existing on-premises infrastructure.
We recommend using an AWS Landing Zone for RISE with SAP connectivity.

Building an AWS Landing Zone
You can implement AWS Landing Zones using AWS Control Tower
In a simple scenario, a Landing Zone contains a minimal footprint focused on connectivity that is typically centred around AWS Transit Gateway. For more information, see Landing zone.
The following is a general overview of the process:
-
Define requirement – understand your organization's security, compliance, and operational requirements. This will help determine the appropriate guardrails, controls, and services to be included in the Landing Zone.
-
Design architecture – plan the overall architecture, including the number of accounts (management, shared services, workload accounts), network design (VPCs, subnets, routing), shared services (logging, monitoring, identity management), and security controls (IAM, service control policies, guardrails).
-
Setup AWS Control Tower – AWS Control Tower helps in setting up and governing a multi-account AWS environment based on best practices. It allows you to create and provision new AWS accounts and deploy baseline security configurations across those accounts.
-
Configure AWS Organizations – Organizations enables you to centrally manage and govern your AWS accounts. Configure Organizations in AWS Control Tower by creating the necessary organizational units (OUs) and service control policies (SCPs).
-
Deploy core accounts and services – create and configure the core accounts, such as the management account, shared services accounts (for logging, security tooling), and any other required shared accounts. Deploy shared services, such as CloudTrail, Config, and Security Hub.
-
Deploy network architecture – set up the network architecture, including VPCs, subnets, route tables, and any necessary network appliances or services (for example, Transit Gateway for a hub-and-spoke model).
-
Configure IAM – establish IAM roles, policies, and groups for controlling access and permissions across the Landing Zone accounts.
-
Implement security controls – deploy security services and guardrails, such as Security Hub, Firewall Manager, AWS WAF, and AWS Config Rules, to enforce security best practices and compliance requirements.
-
Configure logging and monitoring – set up centralized logging and monitoring solutions, such as CloudWatch, CloudTrail, and Config, to capture and analyze logs and events across the Landing Zone accounts.
-
Deploy workload accounts – deploy workload accounts with your Landing Zone. You can create an AWS account to connect to RISE with SAP VPC. We recommended connecting using Transit Gateway for flexibility and ease of management.
-
Automate and maintain – use AWS CloudFormation templates or other Infrastructure as Code tools to automate the deployment and maintenance of the Landing Zone resources. Establish processes for ongoing maintenance, updates, and compliance checks.
AWS Professional
Services
Cost associated to a Customer Managed AWS Landing Zone vary depending on the AWS Services that are used. The AWS Services as described in this paragraph have their own pricing model. For more information on price, see the dedicated pricing pages of the listed AWS Services.