Terjemahan disediakan oleh mesin penerjemah. Jika konten terjemahan yang diberikan bertentangan dengan versi bahasa Inggris aslinya, utamakan versi bahasa Inggris.
AWS KMS penting kriptografi
AWS KMS menggunakan algoritma kriptografi yang dapat dikonfigurasi sehingga sistem dapat dengan cepat bermigrasi dari satu algoritma yang disetujui, atau mode, ke yang lain. Set default awal algoritma kriptografi telah dipilih dari algoritma Federal Information Processing Standard (FIPS-approved) untuk properti keamanan dan kinerjanya.
Entropi dan pembangkitan bilangan acak
AWS KMS Generasi kunci dilakukan di AWS KMS HSMs. HSMsImplementasi generator bilangan acak hibrida yang menggunakan NIST
SP800-90A Deterministic Random Bit Generator (DRBG) CTR_DRBG using AES-256
Operasi kunci simetris (enkripsi saja)
Semua perintah enkripsi kunci simetris yang digunakan dalam HSMs menggunakan Advanced Encryption Standards (AES)
AES- GCM adalah skema enkripsi yang diautentikasi. Selain mengenkripsi plaintext untuk menghasilkan ciphertext, ia menghitung tag otentikasi atas ciphertext dan data tambahan yang otentikasi diperlukan (tambahan data yang diautentikasi, atau). AAD Tag otentikasi membantu memastikan bahwa data berasal dari sumber yang diakui dan bahwa ciphertext dan AAD belum dimodifikasi.
Seringkali, AWS menghilangkan dimasukkannya AAD dalam deskripsi kami, terutama ketika mengacu pada enkripsi kunci data. Hal ini tersirat oleh teks sekitarnya dalam kasus ini bahwa struktur yang akan dienkripsi dipartisi antara plaintext yang akan dienkripsi dan cleartext yang akan dilindungi. AAD
AWS KMS menyediakan opsi bagi Anda untuk mengimpor materi kunci ke dalam AWS KMS key alih-alih mengandalkan AWS KMS untuk menghasilkan materi utama. Bahan kunci impor ini dapat dienkripsi menggunakan RSAES- OAEP
Operasi kunci asimetris (enkripsi, penandatanganan digital dan verifikasi tanda tangan)
AWS KMS mendukung penggunaan operasi kunci asimetris untuk enkripsi, tanda tangan digital, dan operasi perjanjian kunci. Operasi kunci asimetris bergantung pada kunci publik dan private key pair terkait matematis yang dapat Anda gunakan untuk enkripsi dan dekripsi, penandatanganan dan verifikasi tanda tangan, atau memperoleh rahasia bersama. Kunci pribadi tidak pernah meninggalkan yang tidak AWS KMS terenkripsi. Anda dapat menggunakan kunci publik di dalam AWS KMS dengan memanggil AWS KMS API operasi, atau mengunduh kunci publik dan menggunakannya di luar AWS KMS.
AWS KMS mendukung cipher asimetris berikut.
-
RSA- OAEP (untuk enkripsi) & RSA - PSS dan - RSA PKCS - #1 -v1_5 (untuk penandatanganan dan verifikasi) - Mendukung panjang RSA kunci (dalam bit): 2048, 3072, dan 4096 untuk persyaratan keamanan yang berbeda.
-
Elliptic Curve (ECC) — Digunakan untuk penandatanganan dan verifikasi atau memperoleh rahasia bersama, tetapi tidak keduanya. Mendukung ECC kurva: NIST P256, P384, P521, 256k1. SECP
-
SM2(Hanya Wilayah China) — Digunakan untuk enkripsi dan dekripsi, penandatanganan dan verifikasi, atau memperoleh rahasia bersama, tetapi Anda harus memilih satu penggunaan kunci. Mendukung SM2PKE enkripsi dan SM2DSA untuk penandatanganan.
Fungsi derivasi kunci
Fungsi derivasi kunci digunakan untuk mendapatkan kunci tambahan dari rahasia awal atau kunci. AWS KMS menggunakan fungsi derivasi kunci (KDF) untuk mendapatkan kunci per panggilan untuk setiap enkripsi di bawah file. AWS KMS key Semua KDF operasi menggunakan mode KDF in counter
AWS KMS penggunaan internal tanda tangan digital
Tanda tangan digital juga digunakan untuk mengautentikasi perintah dan komunikasi antara entitas AWS KMS . Semua entitas layanan memiliki elliptic curve digital signature algorithm (ECDSA) key pair. Mereka tampil ECDSA seperti yang didefinisikan dalam Penggunaan Algoritma Kriptografi Kurva Elliptik (ECC) dalam Sintaks Pesan Kriptografi (CMS)
Enkripsi amplop
Saat Anda mengenkripsi data, data Anda terlindungi, tetapi Anda harus melindungi kunci enkripsi. Salah satu strateginya adalah dengan mengenkripsikannya. Enkripsi amplop adalah praktik mengenkripsi data plaintext dengan kunci data, kemudian mengenkripsi kunci data di bawah kunci lain.
Anda bahkan dapat mengenkripsi kunci enkripsi data di bawah kunci enkripsi lain, dan mengenkripsi kunci enkripsi tersebut di bawah kunci enkripsi lain. Namun pada akhirnya, satu kunci harus tetap dalam plaintext sehingga Anda dapat mendekripsi kunci dan data Anda. Kunci enkripsi kunci plaintext tingkat atas ini dikenal sebagai kunci root.
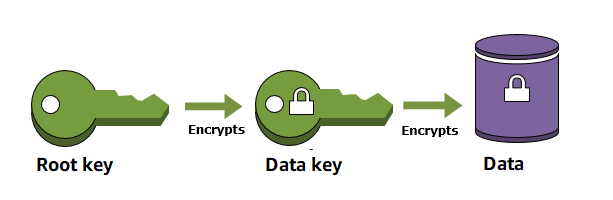
AWS KMS membantu Anda melindungi kunci enkripsi Anda dengan menyimpan dan mengelolanya dengan aman. Kunci root yang disimpan di AWS KMS, dikenal sebagai AWS KMS keys, tidak pernah membiarkan modul keamanan perangkat keras yang AWS KMS FIPS divalidasi
Konstruksi basic yang digunakan dalam banyak sistem kriptografi adalah enkripsi amplop. Enkripsi amplop menggunakan dua kunci kriptografi atau lebih untuk mengamankan pesan. Biasanya, satu kunci berasal dari kunci statis jangka panjang k, dan kunci lainnya adalah kunci per-pesan msgKey, yang dihasilkan untuk mengenkripsi pesan. Amplop dibentuk dengan mengenkripsi pesan: ciphertext = Encrypt (, message). msgKey Kemudian kunci pesan dienkripsi dengan kunci statis jangka panjang: encKey = Enkripsi (k,). msgKey Akhirnya, dua nilai (encKey, ciphertext) dikemas ke dalam struktur tunggal, atau pesan terenkripsi amplop.
Penerima, dengan akses ke k, dapat membuka pesan yang diselimuti dengan terlebih dahulu mendekripsi kunci terenkripsi dan kemudian mendekripsi pesan.
AWS KMS menyediakan kemampuan untuk mengelola kunci statis jangka panjang ini dan mengotomatiskan proses enkripsi amplop data Anda.
Selain kemampuan enkripsi yang disediakan dalam AWS KMS layanan, AWS Enkripsi SDK menyediakan pustaka enkripsi amplop sisi klien. Anda dapat menggunakan perpustakaan ini untuk melindungi data Anda dan kunci enkripsi yang digunakan untuk mengenkripsi data tersebut.
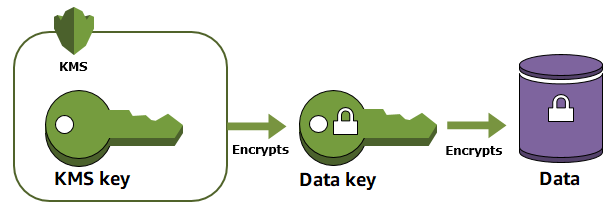
Enkripsi amplop menawarkan beberapa manfaat:
-
Melindungi kunci data
Saat mengenkripsi kunci data, Anda tidak perlu khawatir menyimpan kunci data terenkripsi, karena kunci data terlindung secara inheren oleh enkripsi. Anda dapat menyimpan kunci data terenkripsi dengan aman di samping data yang dienkripsi.
-
Mengenkripsi data yang sama di bawah beberapa kunci
Operasi enkripsi dapat sangat memakan waktu, terutama ketika data yang dienkripsi adalah objek berukuran besar. Alih-alih mengenkripsi ulang data mentah beberapa kali dengan kunci yang berbeda, Anda dapat mengenkripsi ulang hanya kunci data yang melindungi data mentah.
-
Menggabungkan kekuatan beberapa algoritma
Secara umum, algoritme kunci simetris lebih cepat dan menghasilkan ciphertext yang lebih kecil dari algoritme kunci publik. Namun algoritme kunci publik memberikan pemisahan peran yang melekat dan manajemen kunci yang lebih mudah. Enkripsi amplop memungkinkan Anda menggabungkan kekuatan masing-masing strategi.
Operasi kriptografi
Dalam AWS KMS, operasi kriptografi adalah API operasi yang menggunakan KMS kunci untuk melindungi data. Karena KMS kunci tetap berada di dalam AWS KMS, Anda harus memanggil AWS KMS untuk menggunakan KMS kunci dalam operasi kriptografi.
Untuk melakukan operasi kriptografi dengan KMS kunci, gunakan AWS SDKs, AWS Command Line Interface (AWS CLI), atau. Alat AWS untuk PowerShell Anda tidak dapat melakukan operasi kriptografi di konsol AWS KMS . Untuk contoh memanggil operasi kriptografi dalam beberapa bahasa pemrograman, lihat Contoh kode untuk AWS KMS menggunakan AWS SDKs.
Tabel berikut mencantumkan operasi AWS KMS kriptografi. Ini juga menunjukkan jenis kunci dan persyaratan penggunaan kunci untuk KMS kunci yang digunakan dalam operasi.
| Operasi | Tipe Kunci | Penggunaan kunci |
|---|---|---|
| Dekripsi | Simetris atau asimetris | ENCRYPT_DECRYPT |
| DeriveSharedSecret | Asimetris | KEY_AGREEMENT |
| Enkripsi | Simetris atau asimetris | ENCRYPT_DECRYPT |
| GenerateDataKey | Simetris | ENCRYPT_DECRYPT |
| GenerateDataKeyPair | Simetris [1] Tidak didukung pada KMS kunci di toko kunci khusus. |
ENCRYPT_DECRYPT |
| GenerateDataKeyPairWithoutPlaintext | Simetris [1] Tidak didukung pada KMS kunci di toko kunci khusus. |
ENCRYPT_DECRYPT |
| GenerateDataKeyWithoutPlaintext | Simetris | ENCRYPT_DECRYPT |
| GenerateMac | HMAC | GENERATE_VERIFY_MAC |
| GenerateRandom | N/A. Operasi ini tidak menggunakan KMS kunci. | N/A |
| ReEncrypt | Simetris atau asimetris | ENCRYPT_DECRYPT |
| Tanda | Asimetris | SIGN_VERIFY |
| Verifikasi | Asimetris | SIGN_VERIFY |
| VerifyMac | HMAC | GENERATE_VERIFY_MAC |
[1] Menghasilkan data key pair asimetris yang dilindungi oleh kunci enkripsi KMS simetris.
Untuk informasi tentang izin untuk operasi kriptografi, lihat AWS KMS izin.
Untuk membuat AWS KMS responsif dan sangat fungsional untuk semua pengguna, AWS KMS menetapkan kuota pada jumlah operasi kriptografi yang disebut dalam setiap detik. Untuk detailnya, lihat Kuota bersama untuk operasi kriptografis.