Cluster configuration prerequisites
Disable the source/destination check
Each EC2 instance performs source/destination checks by default. This means that the
instance must be the source or destination of any traffic it sends or receives. For
cluster instances, source/destination check must be disabled on both EC2 instances which
are supposed to receive traffic from the Overlay IP address. You can use the AWS CLI
Create a profile for AWS CLI
You need to create a profile for AWS CLI with the following command. This profile helps you run the cluster commands.
aws configure --profile cluster
The profile name must match the configuration of cluster resources, as seen in the following example.
primitive res_AWS_STONITH stonith:external/ec2 \ op start interval=0 timeout=180 \ op stop interval=0 timeout=180 \ op monitor interval=300 timeout=60 \ meta target-role=Started \ params tag=pacemaker profile=cluster pcmk_delay_max=45
AWS roles and policies
The SAP HANA database EC2 instances will run the SLES or RHEL cluster software and its agents. Because SLES and RHEL clustering software and its agents need to access AWS resources to perform failover activities, they need specific AWS IAM privileges.
Create a new IAM role and associate it to the two EC2 instances which are part of the cluster. Attach the following IAM policies to this IAM role.
Create the STONITH
policy
Both instances of the cluster need the privilege to start and stop the other nodes within the cluster. Create a policy as shown in the following example and attach it to the IAM role which is assigned to both cluster instances.
{ "Version": "2012-10-17", "Statement": [ { "Sid": "Stmt1424870324000", "Effect": "Allow", "Action": [ "ec2:DescribeInstances", "ec2:DescribeTags" ], "Resource": "*" }, { "Sid": "Stmt1424870324001", "Effect": "Allow", "Action": [ "ec2:RebootInstances", "ec2:StartInstances", "ec2:StopInstances" ], "Resource": [ "arn:aws:ec2:region-name:account-id:instance/instance-a", "arn:aws:ec2:region-name:account-id:instance/instance-b" ] } ] }, { "Statement": [ { "Effect": "Allow", "Action": [ "EC2:DescribeInstances", "EC2:DescribeVolumes" ], "Resource": "*" }, { "Effect": "Allow", "Action": "cloudwatch:GetMetricStatistics", "Resource": "*" }, { "Effect": "Allow", "Action": "s3:GetObject", "Resource": "arn:aws:s3:::aws-sap-data-provider/config.properties" } ] }
Replace region name, account-id, and instance identifier with the
appropriate values.
Create an overlay IP agent policy
Amazon VPC setup includes assigning subnets to your primary/secondary nodes for the SAP HANA database. Each of
these configured subnets has a classless inter-domain routing (CIDR) IP assignment from
the VPC which resides entirely within one Availability Zone. This CIDR IP assignment
cannot span multiple zones or be reassigned to the secondary instance in a different AZ
during a failover scenario. For this reason,AWS enables you to configure Overlay IP
(OIP) outside of your VPC CIDR block to access the active SAP instance. With IP overlay
routing, you can allow the AWS network to use a non-overlapping RFC1918
For the SLES/RHEL Overlay IP agent to change a routing entry in AWS routing tables, create the following policy and attach to the IAM role which is assigned to both cluster instances:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": "ec2:ReplaceRoute", "Resource": "arn:aws:ec2:region-name:account-id:route-table/rtb-XYZ" }, { "Sid": "VisualEditor1", "Effect": "Allow", "Action": "ec2:DescribeRouteTables", "Resource": "*" } ] }
Replace region name, account-id, and route table identifiers with appropriate values.
Update routing tables
Add a routing entry to the routing tables which are assigned to the subnets of your primary and secondary EC2 instances. This IP address is the virtual IP (overlay IP) address of the SAP HANA cluster which needs to be outside the CIDR range of the VPC. To modify or add a route to a route table using the console:
-
Open the Amazon VPC console at https://console.aws.amazon.com/vpc/
(signin required). -
In the navigation pane, choose Route Tables, and select the route table.
-
Choose Actions > Edit routes.
-
Scroll to the end of the list and click Add another route.
-
Add the overlay IP address in the Destination section and select Elastic Network Interface (ENI) name for one of your existing instances.
-
Save your changes by clicking Save routes.
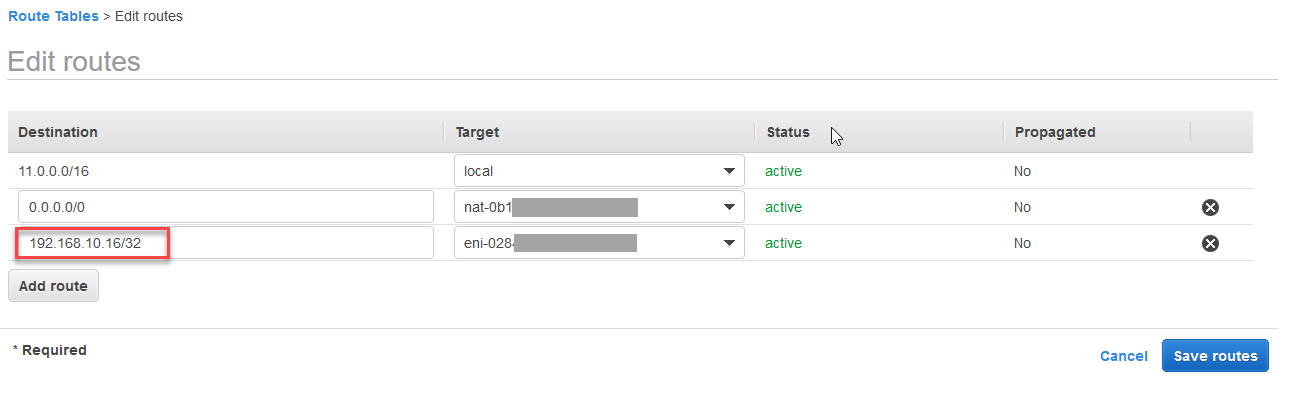
Overlay-IP address entry in route table