翻訳は機械翻訳により提供されています。提供された翻訳内容と英語版の間で齟齬、不一致または矛盾がある場合、英語版が優先します。
ホストされたサイトのファイアウォールサポート
注記
ホストアプリケーションのファイアウォールサポートはプレビューリリースであり、変更される可能性があります。詳細については、「ファイアウォールプレビューの制限」を参照してください。
ファイアウォールのサポートは、オプトインリージョンを除き、Amplify ホスティングが動作 AWS リージョン するすべての でプレビューで現在利用できます。この統合は、 のような AWS WAF グローバルリソースに分類されます CloudFront。ウェブは複数の Amplify ホスティングアプリにアタッチACLsできますが、同じリージョンに存在する必要があります。
ホストされたサイトのファイアウォールのサポートにより、 と直接統合してウェブアプリケーションを保護できます AWS WAF。 AWS WAF を使用すると、ウェブアクセスコントロールリスト (ウェブ ACL) と呼ばれる一連のルールを設定して、定義したカスタマイズ可能なウェブセキュリティルールと条件に基づいてウェブリクエストを許可、ブロック、またはモニタリング (カウント) できます。Amplify アプリを と統合すると AWS WAF、アプリが受け入れるHTTPトラフィックをより詳細に制御し、可視化できます。詳細については AWS WAF、「 AWS WAF デベロッパーガイド」のAWS WAF 「 の仕組み」を参照してください。
を使用して AWS WAF 、SQLインジェクションやクロスサイトスクリプティングなどの一般的なウェブエクスプロイトから Amplify アプリを保護できます。これらは、アプリケーションの可用性とパフォーマンスに影響を与えたり、セキュリティを侵害したり、過剰なリソースを消費したりする可能性があります。例えば、指定された IP アドレス範囲からのリクエスト、 CIDRブロックからのリクエスト、特定の国またはリージョンからのリクエスト、予期しないSQLコードまたはスクリプトを含むリクエストを許可またはブロックするルールを作成できます。
HTTP ヘッダー、メソッド、クエリ文字列、、およびリクエスト本文 (最初の 8 KB に制限) でURI、指定された文字列または正規表現パターンに一致するルールを作成することもできます。さらに、特定のユーザーエージェント、ボット、コンテンツスクレイパーからのイベントをブロックするルールを作成できます。例えば、レートベースのルールを使用して、継続的に更新される後続の 5 分間で、各クライアント IP によって許可されるウェブリクエストの数を指定できます。
サポートされるルールのタイプと追加 AWS WAF 機能の詳細については、 AWS WAF デベロッパーガイドおよび AWS WAF APIリファレンスを参照してください。
重要
セキュリティは、 AWS とお客様の間で共有される責任です。 AWS WAF は、すべてのインターネットセキュリティ問題のソリューションではないため、セキュリティおよびコンプライアンスの目的を満たすように設定する必要があります。の使用時に責任共有モデルを適用する方法を理解するには AWS WAF、AWS WAF 「サービスの使用におけるセキュリティ」を参照してください。
Amplify アプリ AWS WAF の有効化
Firewall 機能を有効にするには、新しいアプリを作成するとき、または既存の Amplify アプリの設定を編集します。どちらのワークフローでも、 AWS WAF ウェブを Amplify ホスティングアプリACLに関連付けます。
Amplify コンソールで既存のアプリ AWS WAF に対して を有効にするには、次の手順に従います。
既存の Amplify アプリ AWS WAF で を有効にする
-
にサインイン AWS Management Console し、 で Amplify コンソールを開きますhttps://console.aws.amazon.com/amplify/
。 -
すべてのアプリページで、デプロイされたアプリの名前を選択してファイアウォール機能を有効にします。
-
ナビゲーションペインで、ホスティングを選択し、ファイアウォールを選択します。
次のスクリーンショットは、Amplify コンソールでファイアウォールの追加ページに移動する方法を示しています。
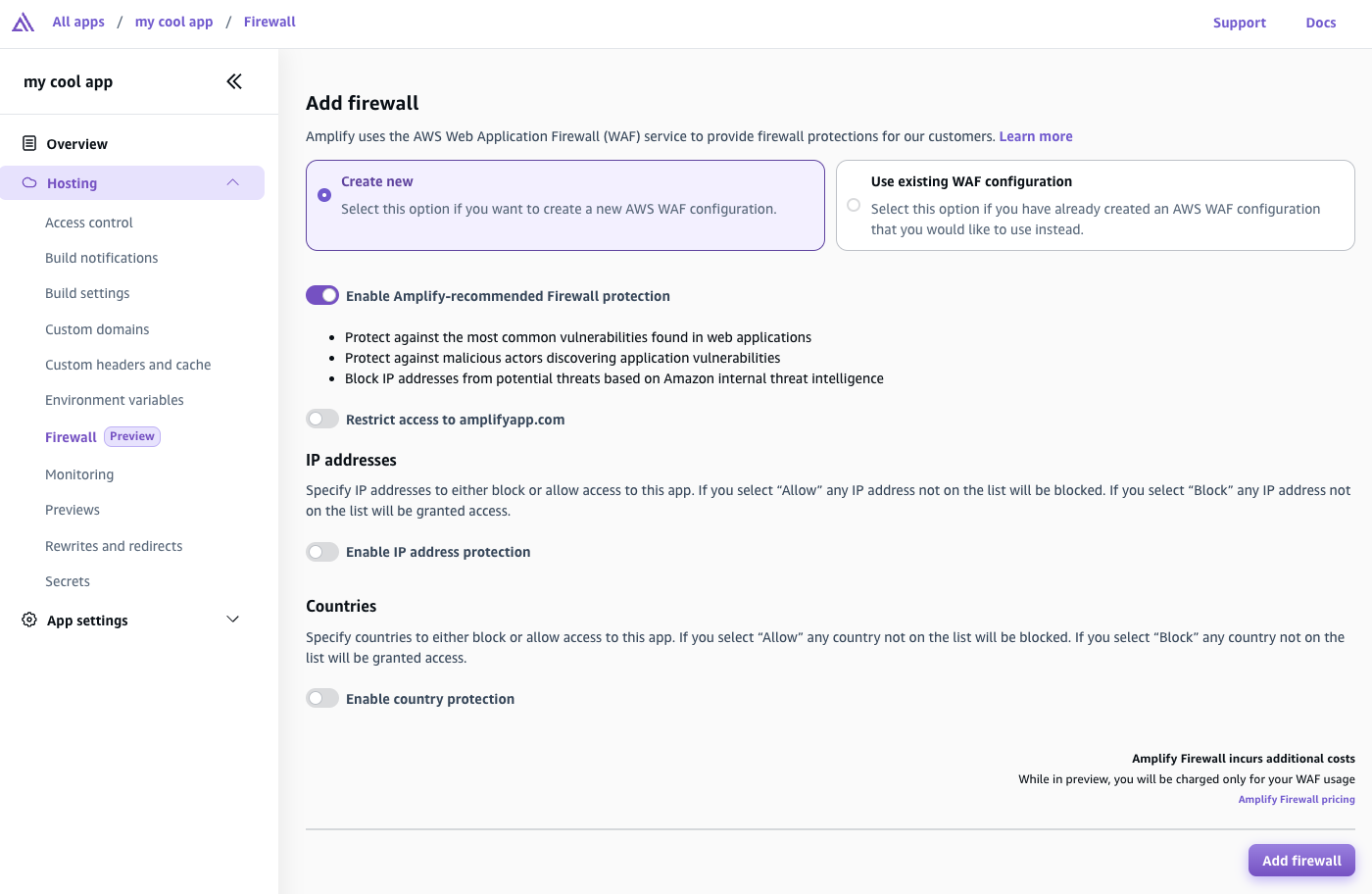
-
ファイアウォールの追加ページで、アクションは、新しい設定を作成するか、既存の AWS WAF 設定を使用するかによって異なります。
-
新しい AWS WAF 設定を作成します。
-
[新規作成] を選択します。
-
必要に応じて、次のいずれかの設定を有効にします。
-
Amplify が推奨するファイアウォール保護を有効にするを有効にします。
-
デフォルトの Amplify ドメインでアプリにアクセスできないように、amplifyapp.com へのアクセスの制限を有効にします。
-
IP アドレスの場合は、IP アドレス保護を有効にする をオンにします。
-
アクション で、アクセス権を持つ IP アドレスを指定し、その他すべての IP アドレスをブロックする場合は許可 を選択します。ブロックされる IP アドレスを指定し、他のすべての IP アドレスにアクセスを許可する場合は、ブロック を選択します。
-
IP バージョンの場合は、 IPV4または を選択しますIPV6。
-
IP アドレステキストボックスに、許可またはブロックされた IP アドレスを CIDR形式で 1 行に 1 つずつ入力します。
-
-
国の場合は、国保護を有効にする をオンにします。
-
アクション で、アクセス権を持つ国を指定し、その他すべての国をブロックする場合は許可 を選択します。ブロックされる国を指定し、他のすべての国にアクセスを許可する場合は、ブロックを選択します。
-
国の場合は、リストから許可またはブロックされている国を選択します。
-
-
次のスクリーンショットは、アプリケーションの新しい AWS WAF 設定を有効にする方法を示しています。
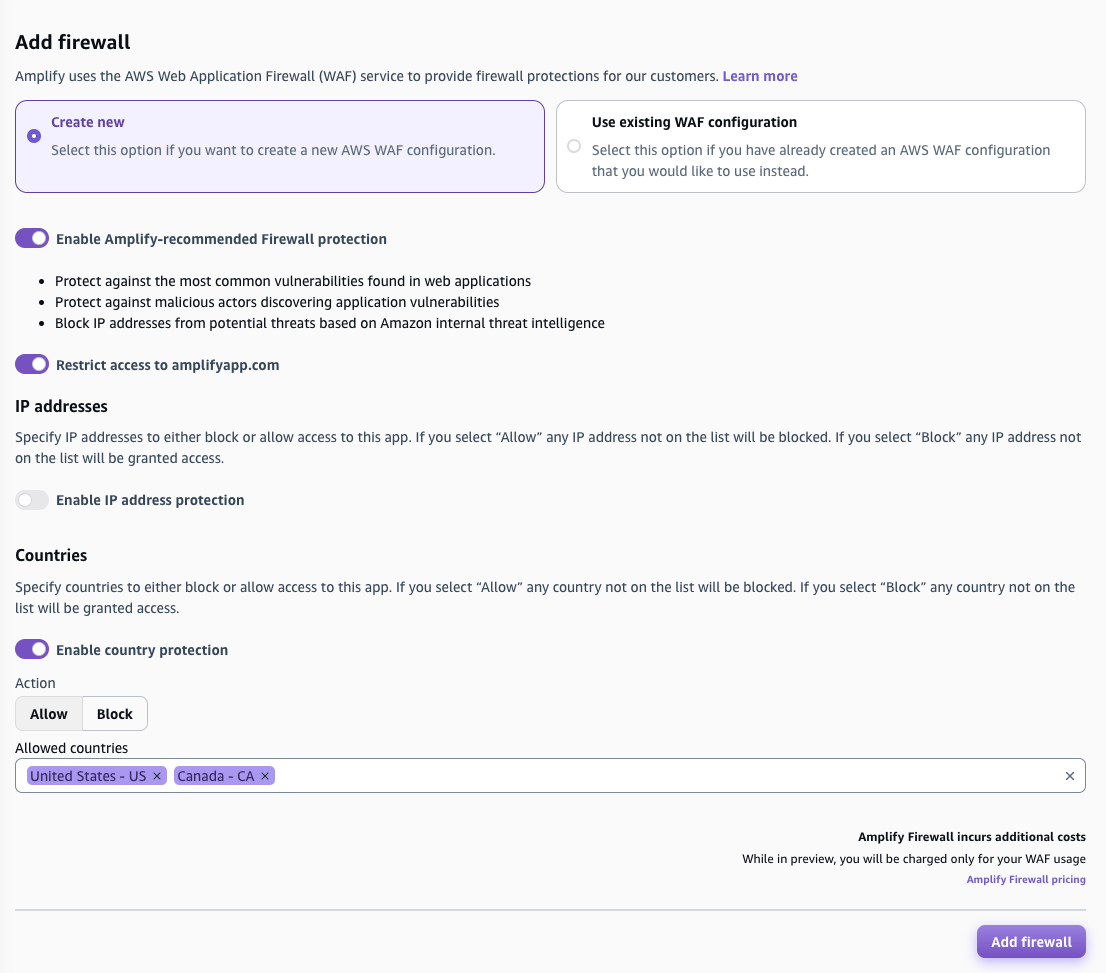
-
-
既存の AWS WAF 設定を使用します。
-
既存の AWS WAF 設定を使用する を選択します。
-
の ACLs AWS WAF にあるウェブのリストから、保存された設定を選択します AWS アカウント。
-
-
-
ファイアウォールの追加 を選択します。
-
ファイアウォールページに、 AWS WAF 設定が伝達されていることを示す関連付けステータスが表示されます。プロセスが完了すると、ステータスは Enabled に変わります。
次のスクリーンショットは、Amplify コンソールのファイアウォールの進行状況ステータスを示しています。これは、 AWS WAF 設定が関連付けられているタイミングと有効になっていることを示します。
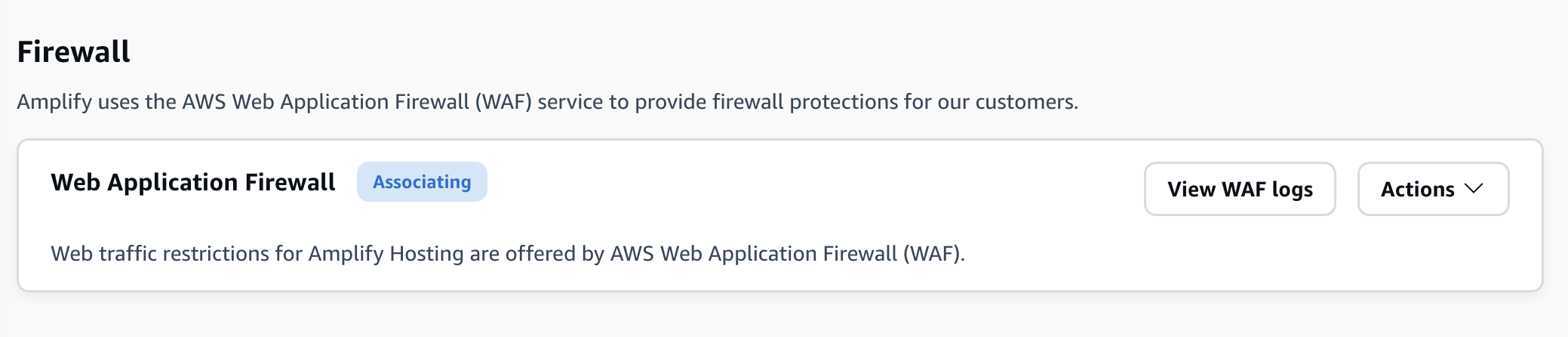
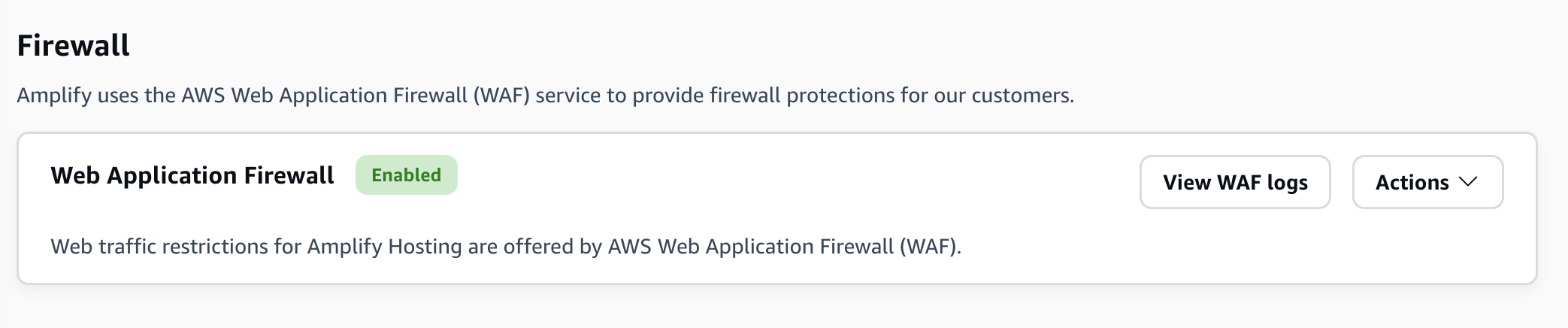
Amplify アプリACLからウェブの関連付けを解除する
Amplify アプリACLに関連付けられているウェブは削除できません。まず、Amplify コンソールでウェブACLとアプリの関連付けを解除する必要があります。その後、 AWS WAF コンソールで削除できます。
Amplify アプリACLからウェブの関連付けを解除するには
-
にサインイン AWS Management Console し、 で Amplify コンソールを開きますhttps://console.aws.amazon.com/amplify/
。 -
すべてのアプリページで、ウェブの関連付けを解除するアプリの名前を選択しますACL。
-
ナビゲーションペインで、ホスティングを選択し、ファイアウォールを選択します。
-
ファイアウォールページで、アクションを選択し、ファイアウォールの関連付けを解除を選択します。
-
確認モーダルで、「」と入力し
disassociate、ファイアウォールの関連付けを解除を選択します。 -
ファイアウォールページで、関連付け解除ステータスが表示され、 AWS WAF 設定が伝達されていることを示します。
プロセスが完了したら、 AWS WAF コンソールACLでウェブを削除できます。
Amplify と の統合方法 AWS WAF
次のリストは、Firewall サポートが とどのように統合されているか AWS WAF 、およびウェブを作成して Amplify アプリACLsに関連付けるときに考慮すべき制約についての詳細を示しています。
-
任意のタイプの Amplify アプリ AWS WAF に対して を有効にできます。これには、サポートされているフレームワーク、サーバー側でレンダリングされた (SSR) アプリ、完全に静的なサイトが含まれます。 AWS WAF は、Amplify Gen 1 および Gen 2 アプリでサポートされています。
-
グローバル (CloudFront) リージョンで Amplify アプリACLsに関連付けるウェブを作成する必要があります。リージョン別ウェブが に既に存在するACLs可能性がありますが AWS アカウント、Amplify と互換性がありません。
-
ウェブACLと Amplify アプリは同じ で作成する必要があります AWS アカウント。を使用して AWS WAF ルール AWS Firewall Manager をレプリケートし AWS アカウント、組織のルールを複数の にまたがって一元化および分散させることを簡素化できます AWS アカウント。詳細については、「 AWS WAF デベロッパーガイド」の 「AWS Firewall Manager」を参照してください。
-
同じ 内のACL複数の Amplify アプリ間で同じウェブを共有できます AWS アカウント。すべてのアプリは同じリージョンに存在する必要があります。
-
ウェブを Amplify アプリに関連付けるACLと、ウェブはデフォルトでアプリ内のすべてのブランチにアACLタッチされます。新しいブランチを作成すると、 にはウェブ が含まれますACL。
-
ウェブを Amplify アプリに関連付けるACLと、そのウェブはアプリのすべてのドメインに自動的に関連付けられます。ただし、ホストヘッダー一致ルールを使用して、単一のドメイン名に適用されるルールを設定できます。
-
Amplify アプリACLに関連付けられているウェブは削除できません。 AWS WAF コンソールACLでウェブを削除する前に、アプリからウェブの関連付けを解除する必要があります。
Amplify ウェブACLリソースポリシー
Amplify がウェブ にアクセスできるようにするにはACL、関連付けACL中にリソースポリシーがウェブにアタッチされます。Amplify はこのリソースポリシーを自動的に構築しますが、 を使用して AWS WAFV2 GetPermissionPolicy表示できますAPI。ウェブを Amplify アプリに関連付けるにはACL、次のIAMアクセス許可が必要です。
-
増幅:AssociateWebACL
-
wafv2:AssociateWebACL
-
wafv2:PutPermissionPolicy
-
wafv2:GetPermissionPolicy
ファイアウォールプレビューの制限
Firewall のプレビューリリースには、次の制限があります。
-
プレビュー期間中、Amplify は との部分的な統合をサポートしています CloudTrail。ウェブACL関連付け中の一部の管理イベントは、 CloudTrail ログに表示されません。
-
プレビュー中にウェブACLが Amplify リソースに関連付けられている場合、この新しい Amplify リソースは AWS WAF コンソールの関連 AWS リソースに表示されません。Amplify を使用してGetAppAPI、アプリケーションACLに関連付けられたウェブを表示できます。Amplify ホスティングコンソールでアプリケーションのファイアウォールページに移動することで、Amplify リソースとファイアウォールの関連付けと関連付け解除を行うことができます。
-
プレビュー中、 AWS Config 統合は利用できません。
-
ファイアウォール機能は、Amplify が現在存在するオプトインリージョンでは使用できません。アジアパシフィック (香港)(ap-east-1)、欧州 (ミラノ)(eu-south-1)、中東 (バーレーン)(me-south-1)。
ファイアウォールの料金
プレビュー中は、 AWS WAF サービスからのみ使用率ベースの料金が発生します。 AWS WAF では、ウェブあたり 5 USD/月、ルールあたり 1 USD が課金ACLされます。少なくとも、2 つのルールACLを持つウェブが 1 つあると仮定して、この統合に対して 7 USD を支払います。料金の詳細については、「AWS WAF の料金
Firewall の機能では、GA で新しい Amplify ホスティングのアドバンスト階層にサブスクライブする必要があり、起動時に追加の機能が含まれます。プレビュー中、ファイアウォールを有効にすると、このアドバンスト階層に自動的にサブスクライブされますが、ファイアウォール機能が一般公開されるまで追加料金は発生しません。ファイアウォールはいつでも削除でき、GA 後に課金されることはありません。この階層の料金の詳細は、GA で通知されます。コミットメントや前払いはありません。