Access Amazon OpenSearch Service using an OpenSearch Service-managed VPC endpoint (AWS PrivateLink)
You can access an Amazon OpenSearch Service domain by setting up an OpenSearch Service-managed VPC endpoint (powered by AWS PrivateLink). These endpoints create a private connection between your VPC and Amazon OpenSearch Service. You can access OpenSearch Service VPC domains as if they were in your VPC, without the use of an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection. Instances in your VPC don't need public IP addresses to access OpenSearch Service.
You can configure OpenSearch Service domains to expose additional endpoints running on public or private subnets within the same VPC, different VPC, or different AWS accounts. This enables you to add an additional layer of security to access your domains regardless of where they run, with no infrastructure to manage. The following diagram illustrates OpenSearch Service-managed VPC endpoints within the same VPC:
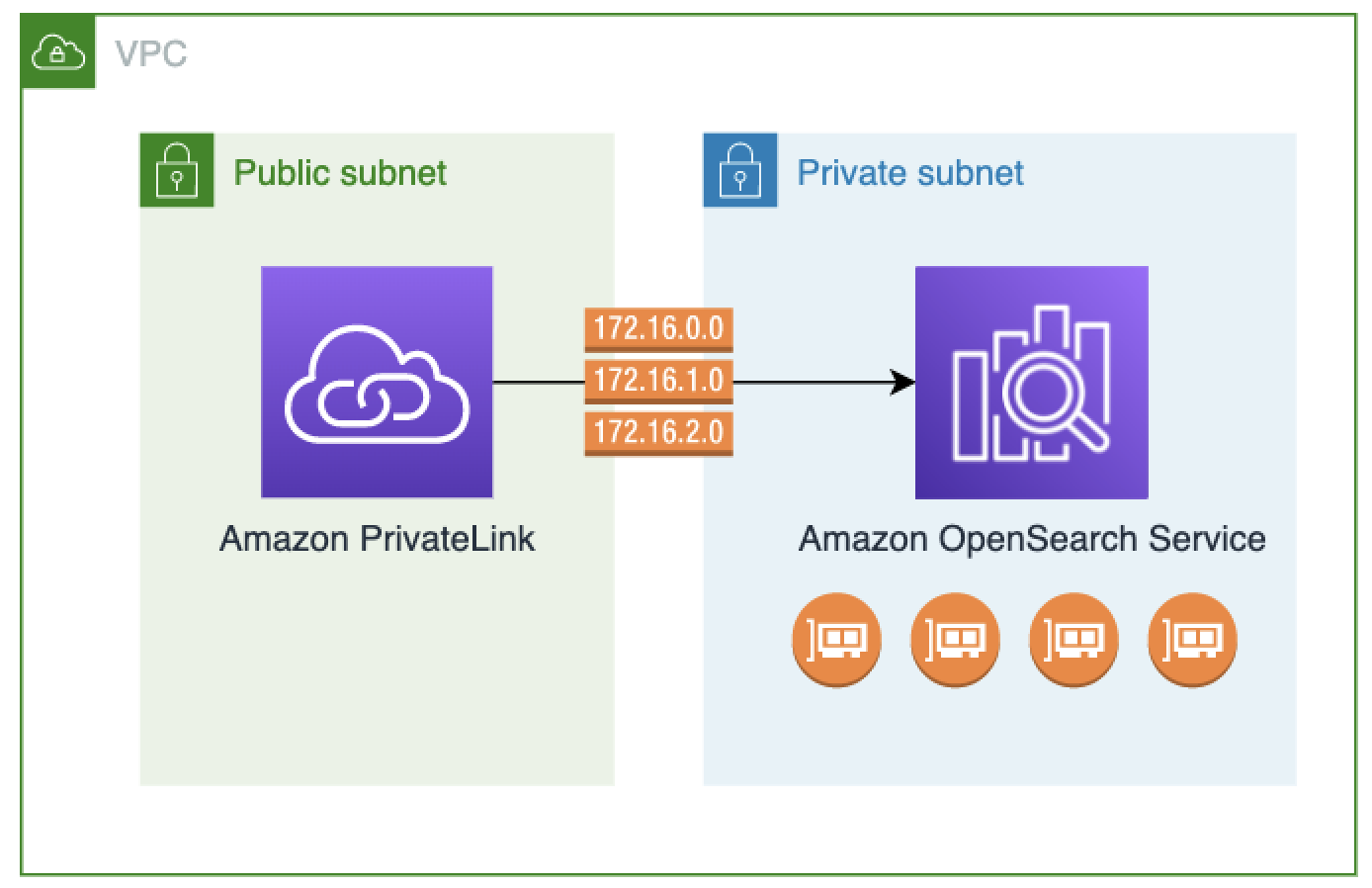
You establish this private connection by creating an OpenSearch Service-managed interface
VPC endpoint, powered by AWS PrivateLink. We create an endpoint network
interface in each subnet that you enable for the interface VPC endpoint. These are
service-managed network interfaces that serve as the entry point for traffic destined for
OpenSearch Service. Standard AWS PrivateLink
interface endpoint pricing
You can create VPC endpoints for domains running all versions of OpenSearch and legacy Elasticsearch. For more information, see Access AWS services through AWS PrivateLink in the AWS PrivateLink Guide.
Considerations and limitations for OpenSearch Service
Before you set up an interface VPC endpoint for OpenSearch Service, review Considerations in the AWS PrivateLink Guide.
When using OpenSearch Service-managed VPC endpoints, consider the following:
-
You can only use interface VPC endpoints to connect to VPC domains. Public domains aren't supported.
-
VPC endpoints can only connect to domains within the same AWS Region.
-
HTTPS is the only supported protocol for VPC endpoints. HTTP is not allowed.
-
OpenSearch Service supports making calls to all of the supported OpenSearch API operations through an interface VPC endpoint.
-
You can configure a maximum of 50 endpoints per account, and a maximum of 10 endpoints per domain. A single domain can have a maximum of 10 authorized principals.
-
You currently can't use AWS CloudFormation to create interface VPC endpoints.
-
You can only create interface VPC endpoints through the OpenSearch Service console or using the OpenSearch Service API. You can't create interface VPC endpoints for OpenSearch Service using the Amazon VPC console.
-
OpenSearch Service-managed VPC endpoints aren't accessible from the internet. An OpenSearch Service-managed VPC endpoint is accessible only within the VPC where the endpoint is provisioned or any VPCs peered with the VPC where the endpoint is provisioned, as permitted by the route tables and security groups.
-
VPC endpoint policies are not supported for OpenSearch Service. You can associate a security group with the endpoint network interfaces to control traffic to OpenSearch Service through the interface VPC endpoint.
-
Your service-linked role must be in the same AWS account that you use to create the VPC endpoint.
-
To create, update, and delete the OpenSearch Service VPC endpoint, you must have the following Amazon EC2 permissions in addition to your Amazon OpenSearch Service permissions:
-
ec2:CreateVpcEndpoint -
ec2:DescribeVpcEndpoints -
ec2:ModifyVpcEndpoint -
ec2:DeleteVpcEndpoints -
ec2:CreateTags -
ec2:DescribeTags -
ec2:DescribeSubnets -
ec2:DescribeSecurityGroups -
ec2:DescribeVpcs
-
Note
Currently, you can't limit VPC endpoint creation to OpenSearch Service. We're working to make this possible in a future update.
Provide access to a domain
If the VPC that you want to access your domain is in another AWS account, you need to authorize it from the owner's account before you can create an interface VPC endpoint.
To allow a VPC in another AWS account to access your domain
Open the Amazon OpenSearch Service console at https://console.aws.amazon.com/aos/home/
. -
In the navigation pane, choose Domains and open the domain that you want to provide access to.
-
Go to the VPC endpoints tab, which shows the accounts and corresponding VPCs that have access to your domain.
-
Choose Authorize principal.
-
Enter the AWS account ID of the account that will access your domain. This step authorizes the specified account to create VPC endpoints against the domain.
-
Choose Authorize.
Create an interface VPC endpoint for a VPC domain
You can create an interface VPC endpoint for OpenSearch Service using either the OpenSearch Service console or the AWS Command Line Interface (AWS CLI).
To create an interface VPC endpoint for an OpenSearch Service domain
Open the Amazon OpenSearch Service console at https://console.aws.amazon.com/aos/home/
. -
In the left navigation pane, choose VPC endpoints.
-
Choose Create endpoint.
-
Select whether to connect a domain in the current AWS account or another AWS account.
-
Select the domain that you connect to with this endpoint. If the domain is in the current AWS account, use the dropdown to choose the domain. If the domain is in a different account, enter the Amazon Resource Name (ARN) of the domain to connect to. To choose a domain in a different account, the owner needs to provide you access to the domain.
-
For VPC, select the VPC from which you'll access OpenSearch Service.
-
For Subnets, select one or more subnets from which you'll access OpenSearch Service.
-
For Security groups, select the security groups to associate with the endpoint network interfaces. This is a critical step in which you limit what ports, protocols, and sources for inbound traffic that you’re authorizing into your endpoint. The security group rules must allow the resources that will use the VPC endpoint to communicate with OpenSearch Service to communicate with the endpoint network interface.
-
Choose Create endpoint. The endpoint should be active within 2-5 minutes.
Working with OpenSearch Service-managed VPC endpoints using the configuration API
Use the following API operations to create and manage OpenSearch Service-managed VPC endpoints.
Use the following API operations to manage endpoint access to VPC domains: