Managing Keys
Amazon EFS is integrated with AWS KMS, which manages the encryption keys for encrypted file systems. AWS KMS also supports encryption by other AWS services such as Amazon Simple Storage Service (Amazon S3), Amazon Elastic Block Store (Amazon EBS), Amazon Relational Database Service (Amazon RDS), Amazon Aurora, Amazon Redshift, Amazon WorkMail, WorkSpaces, etc. To encrypt file system contents, Amazon EFS uses the Advanced Encryption Standard algorithm with XTS Mode and a 256-bit key (XTS-AES-256).
There are three important questions to answer when considering how to secure data at rest by adopting any encryption policy. These questions are equally valid for data stored in managed and unmanaged services such as Amazon EBS.
Where are keys stored?
AWS KMS stores your KMS keys in highly durable storage in an encrypted format to help ensure that they can be retrieved when needed.
Where are keys used?
Using an encrypted Amazon EFS file system is transparent to clients mounting the file system. All cryptographic operations occur within the EFS service, as data is encrypted before it is written to disk and decrypted after a client issues a read request.
Who can use the keys?
AWS KMS key policies control access to encryption keys.
We recommend you combine them with IAM policies to provide another layer of control. Each key has a key policy. If the key is an AWS managed CMK, AWS manages the key policy. If the key is a customer managed CMK, you manage the key policy. These key policies are the primary way to control access to CMKs. They define the permissions that govern the use and management of keys.
When you create an encrypted file system using Amazon EFS, you grant the Amazon EFS access to use the CMK on your behalf. The calls that Amazon EFS makes to AWS KMS on your behalf appear in your CloudTrail logs as though they originated from your AWS account. The following screenshot shows the sample CloudTrail event for a KMS Decrypt call made by Amazon EFS.
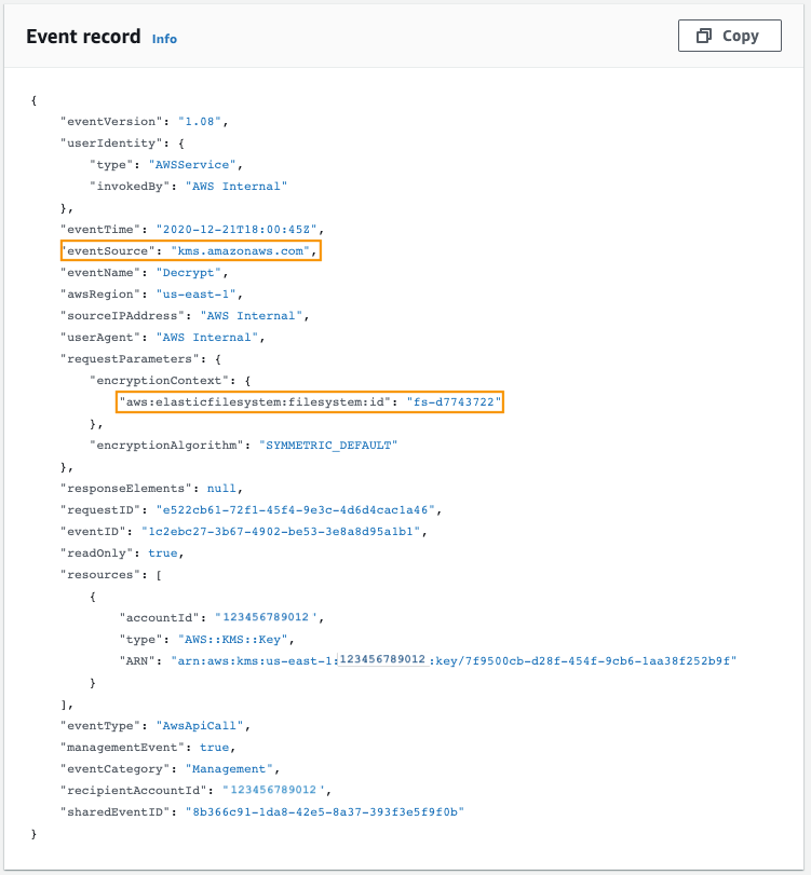
CloudTrail log for KMS Decrypt
For more information about AWS KMS and how to manage access to encryption keys, see Managing Access to AWS KMS CMKs in the AWS KMS Developer Guide.
For more information about how AWS KMS manages cryptography, see the AWS KMS Cryptographic Details whitepaper.
For more information about how to create an administrative user and group, see Create an administrative user in the IAM User Guide.