Migrate Amazon RDS for Oracle to Amazon RDS for PostgreSQL in SSL mode by using AWS DMS
Created by Pinesh Singal (AWS)
Summary
This pattern provides guidance for migrating an Amazon Relational Database Service (Amazon RDS) for Oracle database instance to an Amazon RDS for PostgreSQL database on the Amazon Web Services (AWS) Cloud. To encrypt connections between the databases, the pattern uses certificate authority (CA) and SSL mode in Amazon RDS and AWS Database Migration Service (AWS DMS).
The pattern describes an online migration strategy with little or no downtime for a multi-terabyte Oracle source database with a high number of transactions. For data security, the pattern uses SSL when transferring the data.
This pattern uses AWS Schema Conversion Tool (AWS SCT) to convert the Amazon RDS for Oracle database schema to an Amazon RDS for PostgreSQL schema. Then the pattern uses AWS DMS to migrate data from the Amazon RDS for Oracle database to the Amazon RDS for PostgreSQL database.
Prerequisites and limitations
Prerequisites
An active AWS account
Amazon RDS database certificate authority (CA) configured with rds-ca-rsa2048-g1 only
The rds-ca-2019 certificate expired in August 2024.
The rds-ca-2015 certificate expired on March 5, 2020.
AWS SCT
AWS DMS
pgAdmin
SQL tools (for example, SQL Developer or SQL*Plus)
Limitations
Amazon RDS for Oracle database – The minimum requirement is for Oracle versions 19c for the Enterprise and Standard Two editions.
Amazon RDS for PostgreSQL database – The minimum requirement is for PostgreSQL version 12 and later (for versions 9.x and later).
Product versions
Amazon RDS for Oracle database version 12.1.0.2 instance
Amazon RDS for PostgreSQL database version 11.5 instance
Architecture
Source technology stack
An Amazon RDS for Oracle database instance with version 12.1.0.2.v18.
Target technology stack
AWS DMS
An Amazon RDS for PostgreSQL database instance with version 11.5.
Target architecture
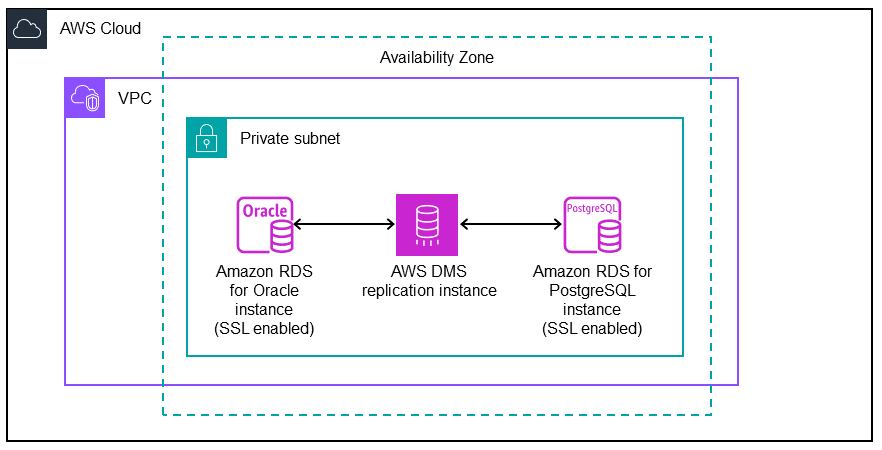
The following diagram shows the architecture for data migration architecture between Oracle (source) and PostgreSQL (target) databases. The architecture includes the following:
A virtual private cloud (VPC)
An Availability Zone
A private subnet
An Amazon RDS for Oracle database
An AWS DMS replication instance
An RDS for PostgreSQL database
To encrypt connections for source and target databases, CA and SSL mode must be enabled in Amazon RDS and AWS DMS.
Tools
AWS services
AWS Database Migration Service (AWS DMS) helps you migrate data stores into the AWS Cloud or between combinations of cloud and on-premises setups.
Amazon Relational Database Service (Amazon RDS) for Oracle helps you set up, operate, and scale an Oracle relational database in the AWS Cloud.
Amazon Relational Database Service (Amazon RDS) for PostgreSQL helps you set up, operate, and scale a PostgreSQL relational database in the AWS Cloud.
AWS Schema Conversion Tool (AWS SCT) supports heterogeneous database migrations by automatically converting the source database schema and a majority of the custom code to a format that’s compatible with the target database.
Other services
pgAdmin
is an open source management tool for PostgreSQL. It provides a graphical interface that helps you create, maintain, and use database objects.
Best practices
Amazon RDS provides new CA certificates as an AWS security best practice. For information about the new certificates and the supported AWS Regions, see Using SSL/TLS to encrypt a connection to a DB instance or cluster.
If your RDS instance is currently on CA certificate rds-ca-2019, and you want to upgrade to rds-ca-rsa2048-g1, follow the instructions in Updating your CA certificate by modifying your DB instance or cluster or Updating your CA certificate by applying maintenance.
Epics
| Task | Description | Skills required |
|---|---|---|
Create the Oracle database instance. | Sign in to your AWS account, open the AWS Management Console, and navigate to the Amazon RDS console. On the console, choose Create database, and then choose Oracle. | General AWS, DBA |
Configure security groups. | Configure inbound and outbound security groups. | General AWS |
Create an option group. | Create an option group in the same VPC and security group as the Amazon RDS for Oracle database. For Option, choose SSL. For Port, choose 2484 (for SSL connections). | General AWS |
Configure the option settings. | Use the following settings:
| General AWS |
Modify the RDS for Oracle DB instance. | Set the CA certificate as rds-ca-rsa2048-g1. Under Option group, attach the previously created option group. | DBA, General AWS |
Confirm that the RDS for Oracle DB instance is available. | Make sure that the Amazon RDS for Oracle database instance is up and running and that the database schema is accessible. To connect to the RDS for Oracle DB, use the
| DBA |
Create objects and data in the RDS for Oracle database. | Create objects and insert data in the schema. | DBA |
| Task | Description | Skills required |
|---|---|---|
Create the RDS for PostgreSQL database. | On the Amazon RDS console Create database page, choose PostgreSQL to create an Amazon RDS for PostgreSQL database instance. | DBA, General AWS |
Configure security groups. | Configure inbound and outbound security groups. | General AWS |
Create a parameter group. | If you are using PostgreSQL version 11.x, create a parameter group to set SSL parameters. In PostgreSQL version 12, the SSL parameter group is enabled by default. | General AWS |
Edit parameters. | Change the By default, the | General AWS |
Modify the RDS for PostgreSQL DB instance. | Set the CA certificate as rds-ca-rsa2048-g1. Attach the default parameter group or the previously created parameter group, depending on your PostgreSQL version. | DBA, General AWS |
Confirm that the RDS for PostgreSQL DB instance is available. | Make sure that the Amazon RDS for PostgreSQL database is up and running. The One option is to set The following output shows that the SSL connection is established.
A second option is to set The following output shows that the SSL connection is established.
| DBA |
| Task | Description | Skills required |
|---|---|---|
Install AWS SCT. | Install the latest version of the AWS SCT application. | General AWS |
Configure AWS SCT with JDBC drivers. | Download the Java Database Connectivity (JDBC) drivers for Oracle (ojdbc8.jar To configure the drivers in AWS SCT, choose Settings, Global settings, Drivers. | General AWS |
Create the AWS SCT project. | Create the AWS SCT project and report, using Oracle as the source DB engine and Amazon RDS for PostgreSQL as the target DB engine:
| General AWS |
Validate database objects. |
| DBA, General AWS |
| Task | Description | Skills required |
|---|---|---|
Create a replication instance. |
| General AWS |
Import the certificate. | Download the certificate bundle (PEM) for your AWS Region. The bundle contains both the | General AWS |
Create the source endpoint. |
For more information, see Using an Oracle database as a source for AWS Database Migration Service. | General AWS |
Create the target endpoint. |
For more information, see Using a PostgreSQL database as a target for AWS Database Migration Service. | General AWS |
Test the endpoints. |
| General AWS |
Create migration tasks. | To create a migration task for full load and change data capture (CDC) or for data validation, do the following:
| General AWS |
Plan the production run. | Confirm downtime with stakeholders such as application owners to run AWS DMS in production systems. | Migration lead |
Run the migration task. |
| General AWS |
Validate the data. | Review migration task results and data in the source Oracle and target PostgreSQL databases:
| DBA |
Stop the migration task. | After you successfully complete the data validation, stop the migration task. | General AWS |
| Task | Description | Skills required |
|---|---|---|
Delete the AWS DMS tasks. |
| General AWS |
Delete the AWS DMS endpoints. | Select the source and target endpoints that you created, choose Actions, and choose Delete. | General AWS |
Delete the AWS DMS replication instance. | Choose the replication instance, choose Actions, and then choose Delete. | General AWS |
Delete the PostgreSQL database. |
| General AWS |
Delete the Oracle database. | On the Amazon RDS console, select the Oracle database instance, choose Actions, and then choose Delete. | General AWS |
Troubleshooting
| Issue | Solution |
|---|---|
AWS SCT source and target test connections are failing. | Configure JDBC driver versions and VPC security group inbound rules to accept the incoming traffic. |
The Oracle source endpoint test run fails. | Check the endpoint settings and whether the replication instance is available. |
The AWS DMS task full-load run fails. | Check whether the source and target databases have matching data types and sizes. |
The AWS DMS validation migration task returns errors. |
|
Related resources
Databases
SSL DB connection
AWS SCT
AWS DMS
Additional information
Amazon RDS Certificate Authority certificates rds-ca-2019 expired in August 2024. If you use or plan to use SSL or TLS with certificate verification to connect to your RDS DB instances or Multi-AZ DB clusters, consider using one of the new CA certificates: rds-ca-rsa2048-g1, rds-ca-rsa4096-g1, or rds-ca-ecc384-g1.