本文為英文版的機器翻譯版本,如內容有任何歧義或不一致之處,概以英文版為準。
使用 Amazon 測試設定 EC2
Amazon Elastic Compute Cloud (Amazon EC2) 在 Amazon Web Services 雲端中提供可擴展的運算容量。您可以使用 Amazon 視需要EC2啟動任意數量或數量的虛擬伺服器、設定安全性和聯網和管理儲存。在此設定中,我們使用 Fleet Manager ,這是 的功能 AWS Systems Manager,以使用遠端桌面通訊協定 () 連線至 Amazon EC2 Windows 執行個體RDP。
本指南示範測試環境,以設定和體驗從 Amazon EC2執行個體到 Amazon Simple Storage Service 的 AWS Management Console 私有存取連線。本教學課程使用 AWS CloudFormation 來建立和設定 Amazon 用來EC2視覺化此功能的網路設定。
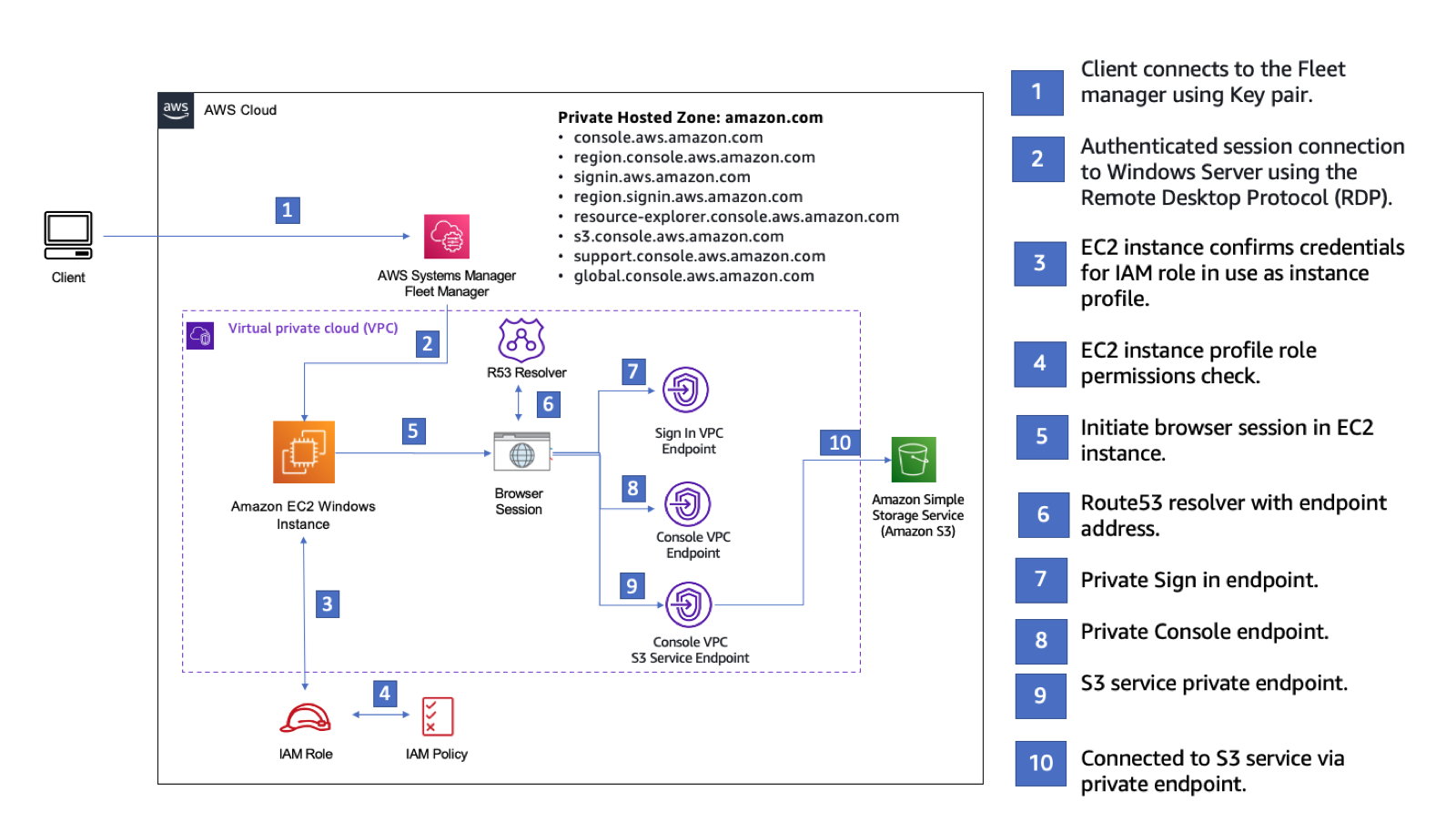
下圖說明使用 Amazon EC2存取 Private Access AWS Management Console 設定的工作流程。它顯示使用者如何使用私有端點連接到 Amazon S3。
複製下列 AWS CloudFormation 範本,並將其儲存到檔案,以供您在設定網路程序的步驟三中使用。
注意
此 AWS CloudFormation 範本使用以色列 (特拉維夫) 區域目前不支援的組態。
Description: | AWS Management Console Private Access. Parameters: VpcCIDR: Type: String Default: 172.16.0.0/16 Description: CIDR range for VPC Ec2KeyPair: Type: AWS::EC2::KeyPair::KeyName Description: The EC2 KeyPair to use to connect to the Windows instance PublicSubnet1CIDR: Type: String Default: 172.16.1.0/24 Description: CIDR range for Public Subnet A PublicSubnet2CIDR: Type: String Default: 172.16.0.0/24 Description: CIDR range for Public Subnet B PublicSubnet3CIDR: Type: String Default: 172.16.2.0/24 Description: CIDR range for Public Subnet C PrivateSubnet1CIDR: Type: String Default: 172.16.4.0/24 Description: CIDR range for Private Subnet A PrivateSubnet2CIDR: Type: String Default: 172.16.5.0/24 Description: CIDR range for Private Subnet B PrivateSubnet3CIDR: Type: String Default: 172.16.3.0/24 Description: CIDR range for Private Subnet C LatestWindowsAmiId: Type: 'AWS::SSM::Parameter::Value<AWS::EC2::Image::Id>' Default: '/aws/service/ami-windows-latest/Windows_Server-2022-English-Full-Base' InstanceTypeParameter: Type: String Default: 't2.medium' Resources: ######################### # VPC AND SUBNETS ######################### AppVPC: Type: 'AWS::EC2::VPC' Properties: CidrBlock: !Ref VpcCIDR InstanceTenancy: default EnableDnsSupport: true EnableDnsHostnames: true PublicSubnetA: Type: 'AWS::EC2::Subnet' Properties: VpcId: !Ref AppVPC CidrBlock: !Ref PublicSubnet1CIDR MapPublicIpOnLaunch: true AvailabilityZone: Fn::Select: - 0 - Fn::GetAZs: "" PublicSubnetB: Type: 'AWS::EC2::Subnet' Properties: VpcId: !Ref AppVPC CidrBlock: !Ref PublicSubnet2CIDR MapPublicIpOnLaunch: true AvailabilityZone: Fn::Select: - 1 - Fn::GetAZs: "" PublicSubnetC: Type: 'AWS::EC2::Subnet' Properties: VpcId: !Ref AppVPC CidrBlock: !Ref PublicSubnet3CIDR MapPublicIpOnLaunch: true AvailabilityZone: Fn::Select: - 2 - Fn::GetAZs: "" PrivateSubnetA: Type: 'AWS::EC2::Subnet' Properties: VpcId: !Ref AppVPC CidrBlock: !Ref PrivateSubnet1CIDR AvailabilityZone: Fn::Select: - 0 - Fn::GetAZs: "" PrivateSubnetB: Type: 'AWS::EC2::Subnet' Properties: VpcId: !Ref AppVPC CidrBlock: !Ref PrivateSubnet2CIDR AvailabilityZone: Fn::Select: - 1 - Fn::GetAZs: "" PrivateSubnetC: Type: 'AWS::EC2::Subnet' Properties: VpcId: !Ref AppVPC CidrBlock: !Ref PrivateSubnet3CIDR AvailabilityZone: Fn::Select: - 2 - Fn::GetAZs: "" InternetGateway: Type: AWS::EC2::InternetGateway InternetGatewayAttachment: Type: AWS::EC2::VPCGatewayAttachment Properties: InternetGatewayId: !Ref InternetGateway VpcId: !Ref AppVPC NatGatewayEIP: Type: AWS::EC2::EIP DependsOn: InternetGatewayAttachment NatGateway: Type: AWS::EC2::NatGateway Properties: AllocationId: !GetAtt NatGatewayEIP.AllocationId SubnetId: !Ref PublicSubnetA ######################### # Route Tables ######################### PrivateRouteTable: Type: 'AWS::EC2::RouteTable' Properties: VpcId: !Ref AppVPC DefaultPrivateRoute: Type: AWS::EC2::Route Properties: RouteTableId: !Ref PrivateRouteTable DestinationCidrBlock: 0.0.0.0/0 NatGatewayId: !Ref NatGateway PrivateSubnetRouteTableAssociation1: Type: 'AWS::EC2::SubnetRouteTableAssociation' Properties: RouteTableId: !Ref PrivateRouteTable SubnetId: !Ref PrivateSubnetA PrivateSubnetRouteTableAssociation2: Type: 'AWS::EC2::SubnetRouteTableAssociation' Properties: RouteTableId: !Ref PrivateRouteTable SubnetId: !Ref PrivateSubnetB PrivateSubnetRouteTableAssociation3: Type: 'AWS::EC2::SubnetRouteTableAssociation' Properties: RouteTableId: !Ref PrivateRouteTable SubnetId: !Ref PrivateSubnetC PublicRouteTable: Type: AWS::EC2::RouteTable Properties: VpcId: !Ref AppVPC DefaultPublicRoute: Type: AWS::EC2::Route DependsOn: InternetGatewayAttachment Properties: RouteTableId: !Ref PublicRouteTable DestinationCidrBlock: 0.0.0.0/0 GatewayId: !Ref InternetGateway PublicSubnetARouteTableAssociation1: Type: AWS::EC2::SubnetRouteTableAssociation Properties: RouteTableId: !Ref PublicRouteTable SubnetId: !Ref PublicSubnetA PublicSubnetBRouteTableAssociation2: Type: AWS::EC2::SubnetRouteTableAssociation Properties: RouteTableId: !Ref PublicRouteTable SubnetId: !Ref PublicSubnetB PublicSubnetBRouteTableAssociation3: Type: AWS::EC2::SubnetRouteTableAssociation Properties: RouteTableId: !Ref PublicRouteTable SubnetId: !Ref PublicSubnetC ######################### # SECURITY GROUPS ######################### VPCEndpointSecurityGroup: Type: 'AWS::EC2::SecurityGroup' Properties: GroupDescription: Allow TLS for VPC Endpoint VpcId: !Ref AppVPC SecurityGroupIngress: - IpProtocol: tcp FromPort: 443 ToPort: 443 CidrIp: !GetAtt AppVPC.CidrBlock EC2SecurityGroup: Type: 'AWS::EC2::SecurityGroup' Properties: GroupDescription: Default EC2 Instance SG VpcId: !Ref AppVPC ######################### # VPC ENDPOINTS ######################### VPCEndpointGatewayS3: Type: 'AWS::EC2::VPCEndpoint' Properties: ServiceName: !Sub 'com.amazonaws.${AWS::Region}.s3' VpcEndpointType: Gateway VpcId: !Ref AppVPC RouteTableIds: - !Ref PrivateRouteTable VPCEndpointInterfaceSSM: Type: 'AWS::EC2::VPCEndpoint' Properties: VpcEndpointType: Interface PrivateDnsEnabled: false SubnetIds: - !Ref PrivateSubnetA - !Ref PrivateSubnetB SecurityGroupIds: - !Ref VPCEndpointSecurityGroup ServiceName: !Sub 'com.amazonaws.${AWS::Region}.ssm' VpcId: !Ref AppVPC VPCEndpointInterfaceEc2messages: Type: 'AWS::EC2::VPCEndpoint' Properties: VpcEndpointType: Interface PrivateDnsEnabled: false SubnetIds: - !Ref PrivateSubnetA - !Ref PrivateSubnetB - !Ref PrivateSubnetC SecurityGroupIds: - !Ref VPCEndpointSecurityGroup ServiceName: !Sub 'com.amazonaws.${AWS::Region}.ec2messages' VpcId: !Ref AppVPC VPCEndpointInterfaceSsmmessages: Type: 'AWS::EC2::VPCEndpoint' Properties: VpcEndpointType: Interface PrivateDnsEnabled: false SubnetIds: - !Ref PrivateSubnetA - !Ref PrivateSubnetB - !Ref PrivateSubnetC SecurityGroupIds: - !Ref VPCEndpointSecurityGroup ServiceName: !Sub 'com.amazonaws.${AWS::Region}.ssmmessages' VpcId: !Ref AppVPC VPCEndpointInterfaceSignin: Type: 'AWS::EC2::VPCEndpoint' Properties: VpcEndpointType: Interface PrivateDnsEnabled: false SubnetIds: - !Ref PrivateSubnetA - !Ref PrivateSubnetB - !Ref PrivateSubnetC SecurityGroupIds: - !Ref VPCEndpointSecurityGroup ServiceName: !Sub 'com.amazonaws.${AWS::Region}.signin' VpcId: !Ref AppVPC VPCEndpointInterfaceConsole: Type: 'AWS::EC2::VPCEndpoint' Properties: VpcEndpointType: Interface PrivateDnsEnabled: false SubnetIds: - !Ref PrivateSubnetA - !Ref PrivateSubnetB - !Ref PrivateSubnetC SecurityGroupIds: - !Ref VPCEndpointSecurityGroup ServiceName: !Sub 'com.amazonaws.${AWS::Region}.console' VpcId: !Ref AppVPC ######################### # ROUTE53 RESOURCES ######################### ConsoleHostedZone: Type: "AWS::Route53::HostedZone" Properties: HostedZoneConfig: Comment: 'Console VPC Endpoint Hosted Zone' Name: 'console.aws.amazon.com' VPCs: - VPCId: !Ref AppVPC VPCRegion: !Ref "AWS::Region" ConsoleRecordGlobal: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'ConsoleHostedZone' Name: 'console.aws.amazon.com' AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] Type: A GlobalConsoleRecord: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'ConsoleHostedZone' Name: 'global.console.aws.amazon.com' AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] Type: A ConsoleS3ProxyRecordGlobal: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'ConsoleHostedZone' Name: 's3.console.aws.amazon.com' AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] Type: A ConsoleSupportProxyRecordGlobal: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'ConsoleHostedZone' Name: "support.console.aws.amazon.com" AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] Type: A ExplorerProxyRecordGlobal: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'ConsoleHostedZone' Name: "resource-explorer.console.aws.amazon.com" AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] Type: A ConsoleRecordRegional: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'ConsoleHostedZone' Name: !Sub "${AWS::Region}.console.aws.amazon.com" AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] Type: A SigninHostedZone: Type: "AWS::Route53::HostedZone" Properties: HostedZoneConfig: Comment: 'Signin VPC Endpoint Hosted Zone' Name: 'signin.aws.amazon.com' VPCs: - VPCId: !Ref AppVPC VPCRegion: !Ref "AWS::Region" SigninRecordGlobal: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'SigninHostedZone' Name: 'signin.aws.amazon.com' AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceSignin.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceSignin.DnsEntries]]] Type: A SigninRecordRegional: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'SigninHostedZone' Name: !Sub "${AWS::Region}.signin.aws.amazon.com" AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceSignin.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceSignin.DnsEntries]]] Type: A ######################### # EC2 INSTANCE ######################### Ec2InstanceRole: Type: AWS::IAM::Role Properties: AssumeRolePolicyDocument: Version: 2012-10-17 Statement: - Effect: Allow Principal: Service: - ec2.amazonaws.com Action: - sts:AssumeRole Path: / ManagedPolicyArns: - arn:aws:iam::aws:policy/AmazonSSMManagedInstanceCore Ec2InstanceProfile: Type: AWS::IAM::InstanceProfile Properties: Path: / Roles: - !Ref Ec2InstanceRole EC2WinInstance: Type: 'AWS::EC2::Instance' Properties: ImageId: !Ref LatestWindowsAmiId IamInstanceProfile: !Ref Ec2InstanceProfile KeyName: !Ref Ec2KeyPair InstanceType: Ref: InstanceTypeParameter SubnetId: !Ref PrivateSubnetA SecurityGroupIds: - Ref: EC2SecurityGroup BlockDeviceMappings: - DeviceName: /dev/sda1 Ebs: VolumeSize: 50 Tags: - Key: "Name" Value: "Console VPCE test instance"
若要設定網路
-
登入您組織的管理帳戶,並開啟 AWS CloudFormation 主控台
。 -
選擇建立堆疊。
-
選擇 With new resources (standard) (使用新資源 (標準))。上傳您先前建立的 AWS CloudFormation 範本檔案,然後選擇下一步。
-
輸入堆疊名稱,例如
PrivateConsoleNetworkForS3,然後選擇 下一步。 -
對於 VPC 和 子網路 ,輸入您偏好的 IP CIDR範圍,或使用提供的預設值。如果您使用預設值,請確認它們不會與 中的現有VPC資源重疊 AWS 帳戶。
-
對於 Ec2KeyPair 參數,請從您帳戶中現有的 Amazon EC2金鑰對中選取一個。如果您沒有現有的 Amazon EC2金鑰對,您必須先建立金鑰對,才能繼續下一個步驟。如需詳細資訊,請參閱 Amazon 使用者指南 中的使用 Amazon 建立金鑰對EC2。 EC2
-
選擇建立堆疊。
-
建立堆疊後,選擇 資源 索引標籤以檢視已建立的資源。
連線至 Amazon EC2執行個體
-
登入您組織的管理帳戶,然後開啟 Amazon EC2主控台
。 -
在導覽窗格中,選擇 Instances (執行個體)。
-
在執行個體頁面上,選取範本建立的主控台VPCE測試執行個體 AWS CloudFormation 。然後選擇 連線。
注意
此範例使用 Fleet Manager 來連線至 Windows Server AWS Systems Manager Explorer,這是 的功能。可能需要幾分鐘才會開始連接。
-
在連線至執行個體頁面上,選擇RDP用戶端 ,然後使用 Fleet Manager 連線。
-
選擇 Fleet Manager 遠端桌面。
-
若要取得 Amazon EC2執行個體的管理密碼並使用 Web 介面存取 Windows 桌面,請使用與您在建立 AWS CloudFormation 範本 時使用的 Amazon 金鑰對相關聯的私有EC2金鑰。
-
從 Amazon EC2 Windows 執行個體中,在瀏覽器 AWS Management Console 中開啟 。
-
使用 AWS 憑證登入後,請開啟 Amazon S3 主控台
,並驗證您是否使用 AWS Management Console Private Access 連線。
測試 AWS Management Console 私有存取設定
-
登入您組織的管理帳戶,並開啟 Amazon S3 主控台
。 -
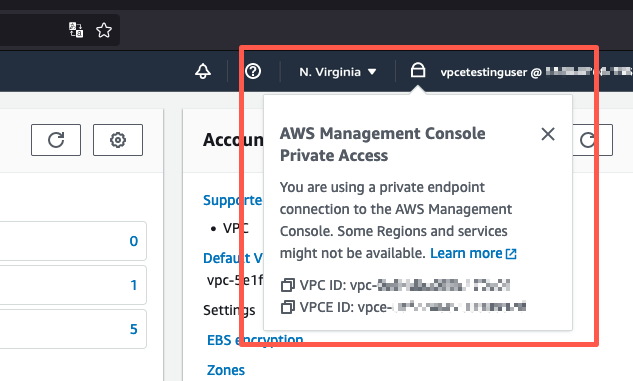
在導覽列中選擇鎖定私有圖示,以檢視正在使用的VPC端點。下列螢幕擷取畫面顯示鎖定私有圖示的位置和VPC資訊。