本文為英文版的機器翻譯版本,如內容有任何歧義或不一致之處,概以英文版為準。
使用 Amazon 測試設定 WorkSpaces
Amazon WorkSpaces 可讓您為使用者佈建虛擬、雲端型 Windows、Amazon Linux 或 Ubuntu Linux 桌面,稱為 WorkSpaces。您可以在需求變更時快速新增或移除使用者。使用者可以從多個裝置或 Web 瀏覽器存取其虛擬桌面。若要進一步了解 WorkSpaces,請參閱 Amazon WorkSpaces 管理指南 。
本節中的範例描述測試環境,其中使用者環境使用在 上執行的 Web 瀏覽器 WorkSpace 登入 AWS Management Console Private Access。然後,使用者會造訪 Amazon Simple Storage Service 主控台。這是 WorkSpace 為了模擬企業使用者在 VPC連線的網路上使用筆記型電腦的體驗, AWS Management Console 從瀏覽器存取 。
本教學課程使用 AWS CloudFormation 來建立和設定網路設定,以及由 使用的 Simple Active Directory WorkSpaces ,以及 WorkSpace 使用 設定 的逐步指示 AWS Management Console。
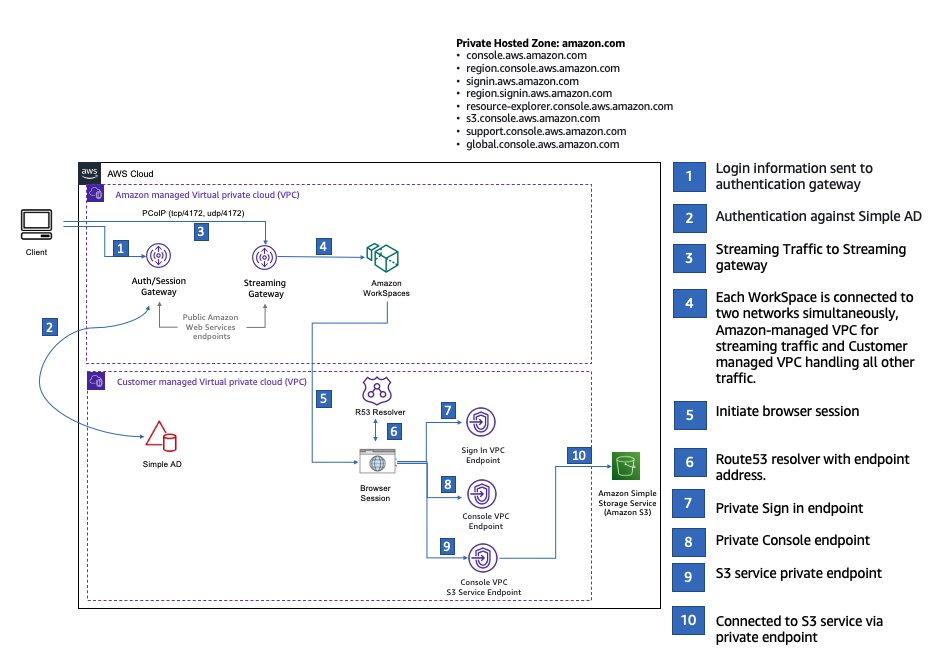
下圖說明使用 WorkSpace 測試 AWS Management Console 私有存取設定的工作流程。它顯示用戶端 WorkSpace、Amazon 受管 VPC和客戶受管 之間的關係VPC。
複製下列 AWS CloudFormation 範本,並將其儲存至您在程序步驟 3 中用來設定網路的檔案。
Description: | AWS Management Console Private Access. Parameters: VpcCIDR: Type: String Default: 172.16.0.0/16 Description: CIDR range for VPC PublicSubnet1CIDR: Type: String Default: 172.16.1.0/24 Description: CIDR range for Public Subnet A PublicSubnet2CIDR: Type: String Default: 172.16.0.0/24 Description: CIDR range for Public Subnet B PrivateSubnet1CIDR: Type: String Default: 172.16.4.0/24 Description: CIDR range for Private Subnet A PrivateSubnet2CIDR: Type: String Default: 172.16.5.0/24 Description: CIDR range for Private Subnet B # Amazon WorkSpaces is available in a subset of the Availability Zones for each supported Region. # https://docs.aws.amazon.com/workspaces/latest/adminguide/azs-workspaces.html Mappings: RegionMap: us-east-1: az1: use1-az2 az2: use1-az4 az3: use1-az6 us-west-2: az1: usw2-az1 az2: usw2-az2 az3: usw2-az3 ap-south-1: az1: aps1-az1 az2: aps1-az2 az3: aps1-az3 ap-northeast-2: az1: apne2-az1 az2: apne2-az3 ap-southeast-1: az1: apse1-az1 az2: apse1-az2 ap-southeast-2: az1: apse2-az1 az2: apse2-az3 ap-northeast-1: az1: apne1-az1 az2: apne1-az4 ca-central-1: az1: cac1-az1 az2: cac1-az2 eu-central-1: az1: euc1-az2 az2: euc1-az3 eu-west-1: az1: euw1-az1 az2: euw1-az2 eu-west-2: az1: euw2-az2 az2: euw2-az3 sa-east-1: az1: sae1-az1 az2: sae1-az3 Resources: iamLambdaExecutionRole: Type: AWS::IAM::Role Properties: AssumeRolePolicyDocument: Version: 2012-10-17 Statement: - Effect: Allow Principal: Service: - lambda.amazonaws.com Action: - 'sts:AssumeRole' ManagedPolicyArns: - arn:aws:iam::aws:policy/service-role/AWSLambdaBasicExecutionRole Policies: - PolicyName: describe-ec2-az PolicyDocument: Version: "2012-10-17" Statement: - Effect: Allow Action: - 'ec2:DescribeAvailabilityZones' Resource: '*' MaxSessionDuration: 3600 Path: /service-role/ fnZoneIdtoZoneName: Type: AWS::Lambda::Function Properties: Runtime: python3.8 Handler: index.lambda_handler Code: ZipFile: | import boto3 import cfnresponse def zoneId_to_zoneName(event, context): responseData = {} ec2 = boto3.client('ec2') describe_az = ec2.describe_availability_zones() for az in describe_az['AvailabilityZones']: if event['ResourceProperties']['ZoneId'] == az['ZoneId']: responseData['ZoneName'] = az['ZoneName'] cfnresponse.send(event, context, cfnresponse.SUCCESS, responseData, str(az['ZoneId'])) def no_op(event, context): print(event) responseData = {} cfnresponse.send(event, context, cfnresponse.SUCCESS, responseData, str(event['RequestId'])) def lambda_handler(event, context): if event['RequestType'] == ('Create' or 'Update'): zoneId_to_zoneName(event, context) else: no_op(event,context) Role: !GetAtt iamLambdaExecutionRole.Arn getAZ1: Type: "Custom::zone-id-zone-name" Properties: ServiceToken: !GetAtt fnZoneIdtoZoneName.Arn ZoneId: !FindInMap [ RegionMap, !Ref 'AWS::Region', az1 ] getAZ2: Type: "Custom::zone-id-zone-name" Properties: ServiceToken: !GetAtt fnZoneIdtoZoneName.Arn ZoneId: !FindInMap [ RegionMap, !Ref 'AWS::Region', az2 ] ######################### # VPC AND SUBNETS ######################### AppVPC: Type: 'AWS::EC2::VPC' Properties: CidrBlock: !Ref VpcCIDR InstanceTenancy: default EnableDnsSupport: true EnableDnsHostnames: true PublicSubnetA: Type: 'AWS::EC2::Subnet' Properties: VpcId: !Ref AppVPC CidrBlock: !Ref PublicSubnet1CIDR MapPublicIpOnLaunch: true AvailabilityZone: !GetAtt getAZ1.ZoneName PublicSubnetB: Type: 'AWS::EC2::Subnet' Properties: VpcId: !Ref AppVPC CidrBlock: !Ref PublicSubnet2CIDR MapPublicIpOnLaunch: true AvailabilityZone: !GetAtt getAZ2.ZoneName PrivateSubnetA: Type: 'AWS::EC2::Subnet' Properties: VpcId: !Ref AppVPC CidrBlock: !Ref PrivateSubnet1CIDR AvailabilityZone: !GetAtt getAZ1.ZoneName PrivateSubnetB: Type: 'AWS::EC2::Subnet' Properties: VpcId: !Ref AppVPC CidrBlock: !Ref PrivateSubnet2CIDR AvailabilityZone: !GetAtt getAZ2.ZoneName InternetGateway: Type: AWS::EC2::InternetGateway InternetGatewayAttachment: Type: AWS::EC2::VPCGatewayAttachment Properties: InternetGatewayId: !Ref InternetGateway VpcId: !Ref AppVPC NatGatewayEIP: Type: AWS::EC2::EIP DependsOn: InternetGatewayAttachment NatGateway: Type: AWS::EC2::NatGateway Properties: AllocationId: !GetAtt NatGatewayEIP.AllocationId SubnetId: !Ref PublicSubnetA ######################### # Route Tables ######################### PrivateRouteTable: Type: 'AWS::EC2::RouteTable' Properties: VpcId: !Ref AppVPC DefaultPrivateRoute: Type: AWS::EC2::Route Properties: RouteTableId: !Ref PrivateRouteTable DestinationCidrBlock: 0.0.0.0/0 NatGatewayId: !Ref NatGateway PrivateSubnetRouteTableAssociation1: Type: 'AWS::EC2::SubnetRouteTableAssociation' Properties: RouteTableId: !Ref PrivateRouteTable SubnetId: !Ref PrivateSubnetA PrivateSubnetRouteTableAssociation2: Type: 'AWS::EC2::SubnetRouteTableAssociation' Properties: RouteTableId: !Ref PrivateRouteTable SubnetId: !Ref PrivateSubnetB PublicRouteTable: Type: AWS::EC2::RouteTable Properties: VpcId: !Ref AppVPC DefaultPublicRoute: Type: AWS::EC2::Route DependsOn: InternetGatewayAttachment Properties: RouteTableId: !Ref PublicRouteTable DestinationCidrBlock: 0.0.0.0/0 GatewayId: !Ref InternetGateway PublicSubnetARouteTableAssociation1: Type: AWS::EC2::SubnetRouteTableAssociation Properties: RouteTableId: !Ref PublicRouteTable SubnetId: !Ref PublicSubnetA PublicSubnetBRouteTableAssociation2: Type: AWS::EC2::SubnetRouteTableAssociation Properties: RouteTableId: !Ref PublicRouteTable SubnetId: !Ref PublicSubnetB ######################### # SECURITY GROUPS ######################### VPCEndpointSecurityGroup: Type: 'AWS::EC2::SecurityGroup' Properties: GroupDescription: Allow TLS for VPC Endpoint VpcId: !Ref AppVPC SecurityGroupIngress: - IpProtocol: tcp FromPort: 443 ToPort: 443 CidrIp: !GetAtt AppVPC.CidrBlock ######################### # VPC ENDPOINTS ######################### VPCEndpointGatewayS3: Type: 'AWS::EC2::VPCEndpoint' Properties: ServiceName: !Sub 'com.amazonaws.${AWS::Region}.s3' VpcEndpointType: Gateway VpcId: !Ref AppVPC RouteTableIds: - !Ref PrivateRouteTable VPCEndpointInterfaceSignin: Type: 'AWS::EC2::VPCEndpoint' Properties: VpcEndpointType: Interface PrivateDnsEnabled: false SubnetIds: - !Ref PrivateSubnetA - !Ref PrivateSubnetB SecurityGroupIds: - !Ref VPCEndpointSecurityGroup ServiceName: !Sub 'com.amazonaws.${AWS::Region}.signin' VpcId: !Ref AppVPC VPCEndpointInterfaceConsole: Type: 'AWS::EC2::VPCEndpoint' Properties: VpcEndpointType: Interface PrivateDnsEnabled: false SubnetIds: - !Ref PrivateSubnetA - !Ref PrivateSubnetB SecurityGroupIds: - !Ref VPCEndpointSecurityGroup ServiceName: !Sub 'com.amazonaws.${AWS::Region}.console' VpcId: !Ref AppVPC ######################### # ROUTE53 RESOURCES ######################### ConsoleHostedZone: Type: "AWS::Route53::HostedZone" Properties: HostedZoneConfig: Comment: 'Console VPC Endpoint Hosted Zone' Name: 'console.aws.amazon.com' VPCs: - VPCId: !Ref AppVPC VPCRegion: !Ref "AWS::Region" ConsoleRecordGlobal: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'ConsoleHostedZone' Name: 'console.aws.amazon.com' AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] Type: A GlobalConsoleRecord: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'ConsoleHostedZone' Name: 'global.console.aws.amazon.com' AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] Type: A ConsoleS3ProxyRecordGlobal: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'ConsoleHostedZone' Name: 's3.console.aws.amazon.com' AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] Type: A ConsoleSupportProxyRecordGlobal: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'ConsoleHostedZone' Name: "support.console.aws.amazon.com" AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] Type: A ExplorerProxyRecordGlobal: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'ConsoleHostedZone' Name: "resource-explorer.console.aws.amazon.com" AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] Type: A ConsoleRecordRegional: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'ConsoleHostedZone' Name: !Sub "${AWS::Region}.console.aws.amazon.com" AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]] Type: A SigninHostedZone: Type: "AWS::Route53::HostedZone" Properties: HostedZoneConfig: Comment: 'Signin VPC Endpoint Hosted Zone' Name: 'signin.aws.amazon.com' VPCs: - VPCId: !Ref AppVPC VPCRegion: !Ref "AWS::Region" SigninRecordGlobal: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'SigninHostedZone' Name: 'signin.aws.amazon.com' AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceSignin.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceSignin.DnsEntries]]] Type: A SigninRecordRegional: Type: AWS::Route53::RecordSet Properties: HostedZoneId: !Ref 'SigninHostedZone' Name: !Sub "${AWS::Region}.signin.aws.amazon.com" AliasTarget: DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceSignin.DnsEntries]]] HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceSignin.DnsEntries]]] Type: A ######################### # WORKSPACE RESOURCES ######################### ADAdminSecret: Type: AWS::SecretsManager::Secret Properties: Name: "ADAdminSecret" Description: "Password for directory services admin" GenerateSecretString: SecretStringTemplate: '{"username": "Admin"}' GenerateStringKey: password PasswordLength: 30 ExcludeCharacters: '"@/\' WorkspaceSimpleDirectory: Type: AWS::DirectoryService::SimpleAD DependsOn: AppVPC DependsOn: PrivateSubnetA DependsOn: PrivateSubnetB Properties: Name: "corp.awsconsole.com" Password: '{{resolve:secretsmanager:ADAdminSecret:SecretString:password}}' Size: "Small" VpcSettings: SubnetIds: - Ref: PrivateSubnetA - Ref: PrivateSubnetB VpcId: Ref: AppVPC Outputs: PrivateSubnetA: Description: Private Subnet A Value: !Ref PrivateSubnetA PrivateSubnetB: Description: Private Subnet B Value: !Ref PrivateSubnetB WorkspaceSimpleDirectory: Description: Directory to be used for Workspaces Value: !Ref WorkspaceSimpleDirectory WorkspacesAdminPassword: Description : "The ARN of the Workspaces admin's password. Navigate to the Secrets Manager in the AWS Console to view the value." Value: !Ref ADAdminSecret
注意
本測試設定會在美國東部 (維吉尼亞北部) 區域中執行。
若要設定網路
-
登入您組織的管理帳戶,並開啟 AWS CloudFormation 主控台
。 -
選擇建立堆疊。
-
選擇 With new resources (standard) (使用新資源 (標準))。上傳您先前建立的 AWS CloudFormation 範本檔案,然後選擇下一步。
-
輸入堆疊名稱,例如
PrivateConsoleNetworkForS3,然後選擇 下一步。 -
對於 VPC 和 子網路 ,輸入您偏好的 IP CIDR範圍,或使用提供的預設值。如果您使用預設值,請確認它們不會與 中的現有VPC資源重疊 AWS 帳戶。
-
選擇建立堆疊。
-
建立堆疊後,選擇 資源 索引標籤以檢視已建立的資源。
-
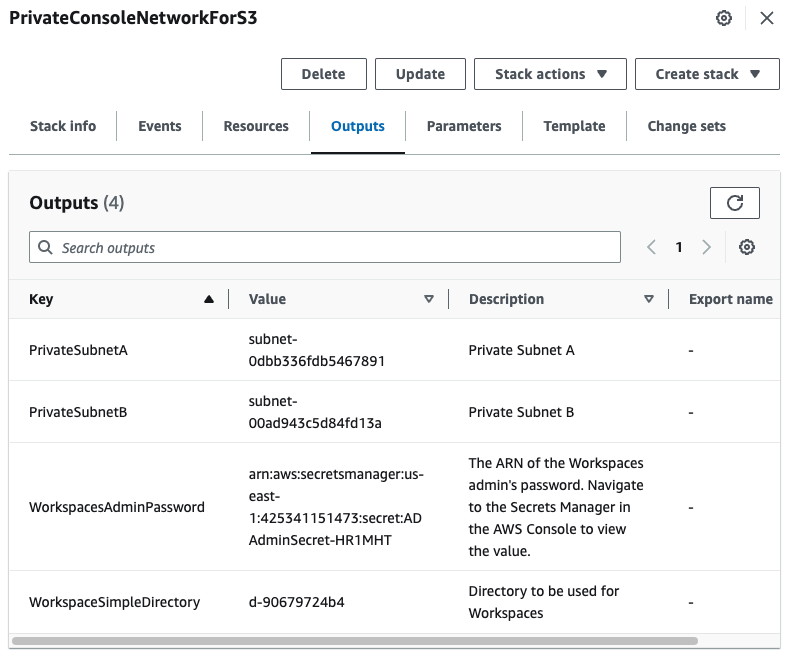
選擇 輸出 索引標籤,以檢視私有子網路和 Workspace Simple Directory 的值。請記下這些值,因為您將在下一個建立和設定 的程序的步驟四中使用它們 WorkSpace。
下列螢幕擷取畫面顯示 輸出 索引標籤的檢視,其中顯示私有子網路和 Workspace Simple Directory 的值。
現在您已建立網路,請使用下列程序來建立和存取 WorkSpace。
若要建立 WorkSpace
-
開啟WorkSpaces 主控台
。 -
在導覽窗格中,選擇目錄。
-
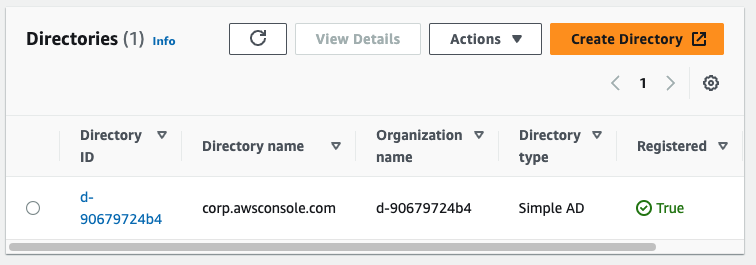
在 目錄 頁面上,確認目錄狀態為 作用中。以下螢幕擷取畫面顯示了作用中目錄的 目錄 頁面。
-
若要在 中使用目錄 WorkSpaces,您必須註冊該目錄。在導覽窗格中,選擇 WorkSpaces,然後選擇建立 WorkSpaces。
-
在 選取目錄 中,請選擇上述程序中由 AWS CloudFormation 建立的目錄。在 動作 功能表上,選擇 註冊。
-
對於子網路選擇,請選取上述程序步驟九中所述的兩個私有子網路。
-
選取 啟用自助服務許可,然後選擇 註冊。
-
目錄註冊後,繼續建立 WorkSpace。選取已註冊的目錄,然後選擇 下一步。
-
在 建立使用者 頁面上選擇 建立其他使用者。輸入您的名稱和電子郵件,以讓您使用 WorkSpace。驗證電子郵件地址是否有效,因為 WorkSpace 登入資訊會傳送到此電子郵件地址。
-
選擇 Next (下一步)。
-
在 識別使用者 頁面上,選取您在步驟九中建立的使用者,然後選擇 下一步。
-
在 選取套件 頁面上,選擇 Standard with Amazon Linux 2,然後選擇 下一步。
-
使用執行模式和使用者自訂的預設設定,檢閱並選擇建立工作區。會以
Pending狀態 WorkSpace 開始,並在Available約 20 分鐘內轉換為 。 -
當 WorkSpace 可用時,您將收到一封電子郵件,其中包含在步驟 9 中提供的電子郵件地址進行存取的指示。
登入您的 後 WorkSpace,您可以使用 AWS Management Console Private Access 測試您是否正在存取它。
若要存取 WorkSpace
-
開啟您在上述程序中的步驟 14 收到的電子郵件。
-
在電子郵件中,選擇提供的唯一連結,以設定您的設定檔並下載 WorkSpaces 用戶端。
-
設定您的密碼。
-
下載您選擇的客戶。
-
安裝並啟動用戶端。輸入電子郵件中提供的註冊碼,然後選擇 註冊。
-
WorkSpaces 使用您在步驟 3 中建立的憑證登入 Amazon。
測試 AWS Management Console 私有存取設定
-
從 WorkSpace開啟瀏覽器。然後,導覽至 AWS Management Console
並使用您的憑據登入。 注意
如果您使用 Firefox 作為瀏覽器,請確認瀏覽器設定中的啟用DNS覆寫HTTPS選項已關閉。
-
開啟 Amazon S3 主控台
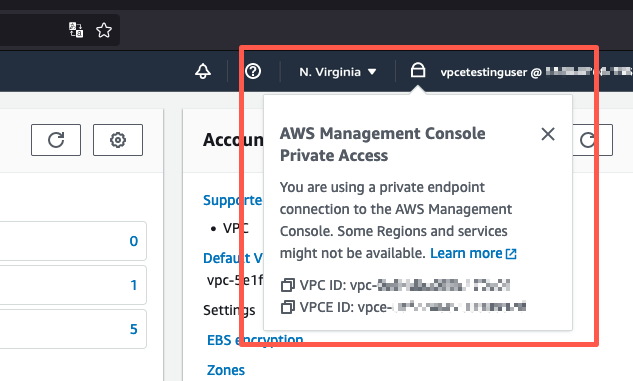
,您可以在其中驗證您是否使用 AWS Management Console Private Access 連線。 -
選擇導覽列上的鎖定私有圖示,以檢視正在使用的 VPC和 VPC 端點。下列螢幕擷取畫面顯示鎖定私有圖示的位置和VPC資訊。