O Amazon Elastic Compute Cloud (Amazon EC2) oferece uma capacidade de computação escalável na Nuvem Amazon Web Services. É possível usar o Amazon EC2 para executar quantos servidores virtuais forem necessários, configurar a segurança e as redes e gerenciar o armazenamento. Nessa configuração, usamos o Fleet Manager, um recurso do AWS Systems Manager, para estabelecer uma conexão com uma instância do Windows do Amazon EC2 usando o Remote Desktop Protocol (RDP).
Este guia demonstra um ambiente de teste para configurar e experimentar uma conexão do Acesso Privado ao AWS Management Console com o Amazon Simple Storage Service por meio de uma instância do Amazon EC2. Este tutorial é usa o AWS CloudFormation para criar e definir a configuração de rede a ser usada pelo Amazon EC2 para visualizar esse recurso.
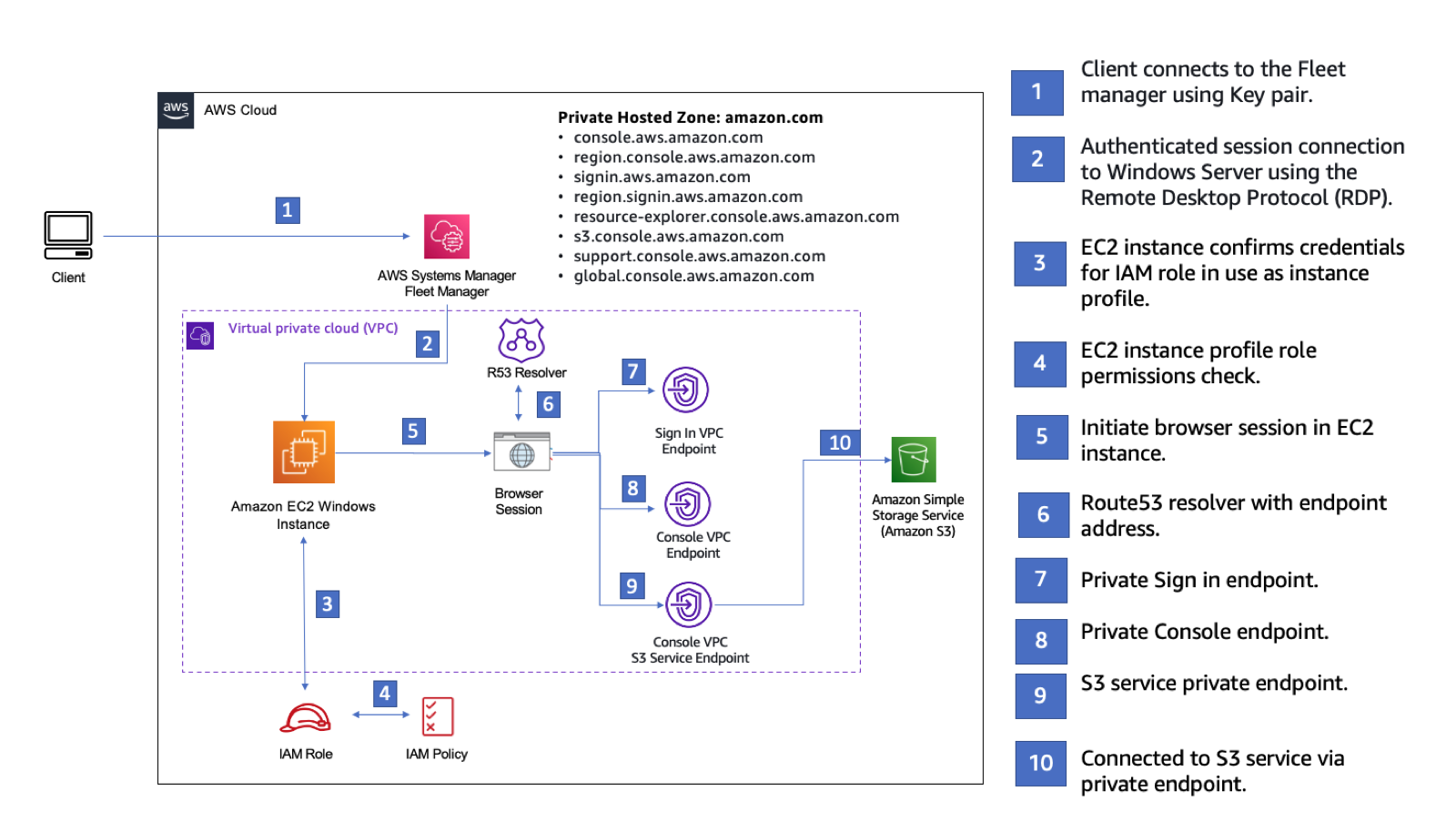
O diagrama a seguir descreve o fluxo de trabalho para acessar uma configuração do Acesso Privado ao AWS Management Console por meio do Amazon EC2. Mostra como um usuário está conectado ao Amazon S3 usando um endpoint privado.
Copie o modelo do AWS CloudFormation a seguir e salve-o em um arquivo que você usará na etapa três do procedimento Para configurar uma rede.
nota
Esse modelo do AWS CloudFormation usa configurações que não são compatíveis no momento com a região de Israel (Tel Aviv).
Description: |
AWS Management Console Private Access.
Parameters:
VpcCIDR:
Type: String
Default: 172.16.0.0/16
Description: CIDR range for VPC
Ec2KeyPair:
Type: AWS::EC2::KeyPair::KeyName
Description: The EC2 KeyPair to use to connect to the Windows instance
PublicSubnet1CIDR:
Type: String
Default: 172.16.1.0/24
Description: CIDR range for Public Subnet A
PublicSubnet2CIDR:
Type: String
Default: 172.16.0.0/24
Description: CIDR range for Public Subnet B
PublicSubnet3CIDR:
Type: String
Default: 172.16.2.0/24
Description: CIDR range for Public Subnet C
PrivateSubnet1CIDR:
Type: String
Default: 172.16.4.0/24
Description: CIDR range for Private Subnet A
PrivateSubnet2CIDR:
Type: String
Default: 172.16.5.0/24
Description: CIDR range for Private Subnet B
PrivateSubnet3CIDR:
Type: String
Default: 172.16.3.0/24
Description: CIDR range for Private Subnet C
LatestWindowsAmiId:
Type: 'AWS::SSM::Parameter::Value<AWS::EC2::Image::Id>'
Default: '/aws/service/ami-windows-latest/Windows_Server-2022-English-Full-Base'
InstanceTypeParameter:
Type: String
Default: 't2.medium'
Resources:
#########################
# VPC AND SUBNETS
#########################
AppVPC:
Type: 'AWS::EC2::VPC'
Properties:
CidrBlock: !Ref VpcCIDR
InstanceTenancy: default
EnableDnsSupport: true
EnableDnsHostnames: true
PublicSubnetA:
Type: 'AWS::EC2::Subnet'
Properties:
VpcId: !Ref AppVPC
CidrBlock: !Ref PublicSubnet1CIDR
MapPublicIpOnLaunch: true
AvailabilityZone:
Fn::Select:
- 0
- Fn::GetAZs: ""
PublicSubnetB:
Type: 'AWS::EC2::Subnet'
Properties:
VpcId: !Ref AppVPC
CidrBlock: !Ref PublicSubnet2CIDR
MapPublicIpOnLaunch: true
AvailabilityZone:
Fn::Select:
- 1
- Fn::GetAZs: ""
PublicSubnetC:
Type: 'AWS::EC2::Subnet'
Properties:
VpcId: !Ref AppVPC
CidrBlock: !Ref PublicSubnet3CIDR
MapPublicIpOnLaunch: true
AvailabilityZone:
Fn::Select:
- 2
- Fn::GetAZs: ""
PrivateSubnetA:
Type: 'AWS::EC2::Subnet'
Properties:
VpcId: !Ref AppVPC
CidrBlock: !Ref PrivateSubnet1CIDR
AvailabilityZone:
Fn::Select:
- 0
- Fn::GetAZs: ""
PrivateSubnetB:
Type: 'AWS::EC2::Subnet'
Properties:
VpcId: !Ref AppVPC
CidrBlock: !Ref PrivateSubnet2CIDR
AvailabilityZone:
Fn::Select:
- 1
- Fn::GetAZs: ""
PrivateSubnetC:
Type: 'AWS::EC2::Subnet'
Properties:
VpcId: !Ref AppVPC
CidrBlock: !Ref PrivateSubnet3CIDR
AvailabilityZone:
Fn::Select:
- 2
- Fn::GetAZs: ""
InternetGateway:
Type: AWS::EC2::InternetGateway
InternetGatewayAttachment:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
InternetGatewayId: !Ref InternetGateway
VpcId: !Ref AppVPC
NatGatewayEIP:
Type: AWS::EC2::EIP
DependsOn: InternetGatewayAttachment
NatGateway:
Type: AWS::EC2::NatGateway
Properties:
AllocationId: !GetAtt NatGatewayEIP.AllocationId
SubnetId: !Ref PublicSubnetA
#########################
# Route Tables
#########################
PrivateRouteTable:
Type: 'AWS::EC2::RouteTable'
Properties:
VpcId: !Ref AppVPC
DefaultPrivateRoute:
Type: AWS::EC2::Route
Properties:
RouteTableId: !Ref PrivateRouteTable
DestinationCidrBlock: 0.0.0.0/0
NatGatewayId: !Ref NatGateway
PrivateSubnetRouteTableAssociation1:
Type: 'AWS::EC2::SubnetRouteTableAssociation'
Properties:
RouteTableId: !Ref PrivateRouteTable
SubnetId: !Ref PrivateSubnetA
PrivateSubnetRouteTableAssociation2:
Type: 'AWS::EC2::SubnetRouteTableAssociation'
Properties:
RouteTableId: !Ref PrivateRouteTable
SubnetId: !Ref PrivateSubnetB
PrivateSubnetRouteTableAssociation3:
Type: 'AWS::EC2::SubnetRouteTableAssociation'
Properties:
RouteTableId: !Ref PrivateRouteTable
SubnetId: !Ref PrivateSubnetC
PublicRouteTable:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref AppVPC
DefaultPublicRoute:
Type: AWS::EC2::Route
DependsOn: InternetGatewayAttachment
Properties:
RouteTableId: !Ref PublicRouteTable
DestinationCidrBlock: 0.0.0.0/0
GatewayId: !Ref InternetGateway
PublicSubnetARouteTableAssociation1:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PublicRouteTable
SubnetId: !Ref PublicSubnetA
PublicSubnetBRouteTableAssociation2:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PublicRouteTable
SubnetId: !Ref PublicSubnetB
PublicSubnetBRouteTableAssociation3:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PublicRouteTable
SubnetId: !Ref PublicSubnetC
#########################
# SECURITY GROUPS
#########################
VPCEndpointSecurityGroup:
Type: 'AWS::EC2::SecurityGroup'
Properties:
GroupDescription: Allow TLS for VPC Endpoint
VpcId: !Ref AppVPC
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: 443
ToPort: 443
CidrIp: !GetAtt AppVPC.CidrBlock
EC2SecurityGroup:
Type: 'AWS::EC2::SecurityGroup'
Properties:
GroupDescription: Default EC2 Instance SG
VpcId: !Ref AppVPC
#########################
# VPC ENDPOINTS
#########################
VPCEndpointGatewayS3:
Type: 'AWS::EC2::VPCEndpoint'
Properties:
ServiceName: !Sub 'com.amazonaws.${AWS::Region}.s3'
VpcEndpointType: Gateway
VpcId: !Ref AppVPC
RouteTableIds:
- !Ref PrivateRouteTable
VPCEndpointInterfaceSSM:
Type: 'AWS::EC2::VPCEndpoint'
Properties:
VpcEndpointType: Interface
PrivateDnsEnabled: false
SubnetIds:
- !Ref PrivateSubnetA
- !Ref PrivateSubnetB
SecurityGroupIds:
- !Ref VPCEndpointSecurityGroup
ServiceName: !Sub 'com.amazonaws.${AWS::Region}.ssm'
VpcId: !Ref AppVPC
VPCEndpointInterfaceEc2messages:
Type: 'AWS::EC2::VPCEndpoint'
Properties:
VpcEndpointType: Interface
PrivateDnsEnabled: false
SubnetIds:
- !Ref PrivateSubnetA
- !Ref PrivateSubnetB
- !Ref PrivateSubnetC
SecurityGroupIds:
- !Ref VPCEndpointSecurityGroup
ServiceName: !Sub 'com.amazonaws.${AWS::Region}.ec2messages'
VpcId: !Ref AppVPC
VPCEndpointInterfaceSsmmessages:
Type: 'AWS::EC2::VPCEndpoint'
Properties:
VpcEndpointType: Interface
PrivateDnsEnabled: false
SubnetIds:
- !Ref PrivateSubnetA
- !Ref PrivateSubnetB
- !Ref PrivateSubnetC
SecurityGroupIds:
- !Ref VPCEndpointSecurityGroup
ServiceName: !Sub 'com.amazonaws.${AWS::Region}.ssmmessages'
VpcId: !Ref AppVPC
VPCEndpointInterfaceSignin:
Type: 'AWS::EC2::VPCEndpoint'
Properties:
VpcEndpointType: Interface
PrivateDnsEnabled: false
SubnetIds:
- !Ref PrivateSubnetA
- !Ref PrivateSubnetB
- !Ref PrivateSubnetC
SecurityGroupIds:
- !Ref VPCEndpointSecurityGroup
ServiceName: !Sub 'com.amazonaws.${AWS::Region}.signin'
VpcId: !Ref AppVPC
VPCEndpointInterfaceConsole:
Type: 'AWS::EC2::VPCEndpoint'
Properties:
VpcEndpointType: Interface
PrivateDnsEnabled: false
SubnetIds:
- !Ref PrivateSubnetA
- !Ref PrivateSubnetB
- !Ref PrivateSubnetC
SecurityGroupIds:
- !Ref VPCEndpointSecurityGroup
ServiceName: !Sub 'com.amazonaws.${AWS::Region}.console'
VpcId: !Ref AppVPC
#########################
# ROUTE53 RESOURCES
#########################
ConsoleHostedZone:
Type: "AWS::Route53::HostedZone"
Properties:
HostedZoneConfig:
Comment: 'Console VPC Endpoint Hosted Zone'
Name: 'console.aws.amazon.com'
VPCs:
-
VPCId: !Ref AppVPC
VPCRegion: !Ref "AWS::Region"
ConsoleRecordGlobal:
Type: AWS::Route53::RecordSet
Properties:
HostedZoneId: !Ref 'ConsoleHostedZone'
Name: 'console.aws.amazon.com'
AliasTarget:
DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]]
HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]]
Type: A
GlobalConsoleRecord:
Type: AWS::Route53::RecordSet
Properties:
HostedZoneId: !Ref 'ConsoleHostedZone'
Name: 'global.console.aws.amazon.com'
AliasTarget:
DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]]
HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]]
Type: A
ConsoleS3ProxyRecordGlobal:
Type: AWS::Route53::RecordSet
Properties:
HostedZoneId: !Ref 'ConsoleHostedZone'
Name: 's3.console.aws.amazon.com'
AliasTarget:
DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]]
HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]]
Type: A
ConsoleSupportProxyRecordGlobal:
Type: AWS::Route53::RecordSet
Properties:
HostedZoneId: !Ref 'ConsoleHostedZone'
Name: "support.console.aws.amazon.com"
AliasTarget:
DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]]
HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]]
Type: A
ExplorerProxyRecordGlobal:
Type: AWS::Route53::RecordSet
Properties:
HostedZoneId: !Ref 'ConsoleHostedZone'
Name: "resource-explorer.console.aws.amazon.com"
AliasTarget:
DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]]
HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]]
Type: A
ConsoleRecordRegional:
Type: AWS::Route53::RecordSet
Properties:
HostedZoneId: !Ref 'ConsoleHostedZone'
Name: !Sub "${AWS::Region}.console.aws.amazon.com"
AliasTarget:
DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]]
HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceConsole.DnsEntries]]]
Type: A
SigninHostedZone:
Type: "AWS::Route53::HostedZone"
Properties:
HostedZoneConfig:
Comment: 'Signin VPC Endpoint Hosted Zone'
Name: 'signin.aws.amazon.com'
VPCs:
-
VPCId: !Ref AppVPC
VPCRegion: !Ref "AWS::Region"
SigninRecordGlobal:
Type: AWS::Route53::RecordSet
Properties:
HostedZoneId: !Ref 'SigninHostedZone'
Name: 'signin.aws.amazon.com'
AliasTarget:
DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceSignin.DnsEntries]]]
HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceSignin.DnsEntries]]]
Type: A
SigninRecordRegional:
Type: AWS::Route53::RecordSet
Properties:
HostedZoneId: !Ref 'SigninHostedZone'
Name: !Sub "${AWS::Region}.signin.aws.amazon.com"
AliasTarget:
DNSName: !Select ['1', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceSignin.DnsEntries]]]
HostedZoneId: !Select ['0', !Split [':', !Select ['0', !GetAtt VPCEndpointInterfaceSignin.DnsEntries]]]
Type: A
#########################
# EC2 INSTANCE
#########################
Ec2InstanceRole:
Type: AWS::IAM::Role
Properties:
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
-
Effect: Allow
Principal:
Service:
- ec2.amazonaws.com
Action:
- sts:AssumeRole
Path: /
ManagedPolicyArns:
- arn:aws:iam::aws:policy/AmazonSSMManagedInstanceCore
Ec2InstanceProfile:
Type: AWS::IAM::InstanceProfile
Properties:
Path: /
Roles:
- !Ref Ec2InstanceRole
EC2WinInstance:
Type: 'AWS::EC2::Instance'
Properties:
ImageId: !Ref LatestWindowsAmiId
IamInstanceProfile: !Ref Ec2InstanceProfile
KeyName: !Ref Ec2KeyPair
InstanceType:
Ref: InstanceTypeParameter
SubnetId: !Ref PrivateSubnetA
SecurityGroupIds:
- Ref: EC2SecurityGroup
BlockDeviceMappings:
- DeviceName: /dev/sda1
Ebs:
VolumeSize: 50
Tags:
- Key: "Name"
Value: "Console VPCE test instance"
Para configurar uma rede
-
Faça login na conta de gerenciamento da organização e abra o console do AWS CloudFormation
. -
Selecione Criar pilha.
-
Escolha With new resources (standard) (Com novos recursos [padrão]). Faça upload do arquivo de modelo do AWS CloudFormation que você criou anteriormente e escolha Próximo.
-
Insira um nome para a pilha, por exemplo
PrivateConsoleNetworkForS3, e escolha Próximo. -
Em VPC e sub-redes, insira os intervalos CIDR de IP de sua preferência ou use os valores padrão fornecidos. Se você usar os valores padrão, verifique se eles não se sobrepõem aos recursos de VPC existentes em sua Conta da AWS.
-
Para o parâmetro Ec2KeyPair, selecione um dos pares de chaves do Amazon EC2 existentes em sua conta. Se você ainda não tiver um par de chaves do Amazon EC2, deverá criar um antes de passar para a próxima etapa. Para ter mais informações, consulte Criar um par de chaves usando o Amazon EC2 no Guia do usuário do Amazon EC2.
-
Selecione Criar pilha.
-
Depois que a pilha for criada, escolha a guia Recursos para ver os recursos que foram criados.
Para se conectar à instância do Amazon EC2
-
Faça login na conta de gerenciamento da organização e abra o console do Amazon EC2
. -
No painel de navegação, escolha Instances (Instâncias).
-
Na página Instâncias, selecione Instância de teste do Console VPCE que foi criada pelo modelo do AWS CloudFormation. Depois, escolha Conectar.
nota
Este exemplo usa o Fleet Manager, um recurso do AWS Systems Manager Explorer, para se conectar ao Windows Server. Pode levar alguns minutos até a conexão ser iniciada.
-
Na página Conectar-se à instância, escolha Cliente RDP e Conectar-se usando o Fleet Manager.
-
Escolha Fleet Manager: área de trabalho remota.
-
Para obter a senha administrativa da instância do Amazon EC2 e acessar a área de trabalho do Windows usando a interface da web, utilize a chave privada associada ao par de chaves do Amazon EC2 que você usou ao criar o modelo do AWS CloudFormation.
-
Na instância do Windows do Amazon EC2, abra o AWS Management Console no navegador.
-
Depois de fazer login com suas credenciais da AWS, abra o console do Amazon S3
e verifique se você está conectado usando o Acesso Privado ao AWS Management Console.
Para testar a configuração do Acesso Privado ao AWS Management Console
-
Faça login na conta de gerenciamento da organização e abra o console do Amazon S3
. -
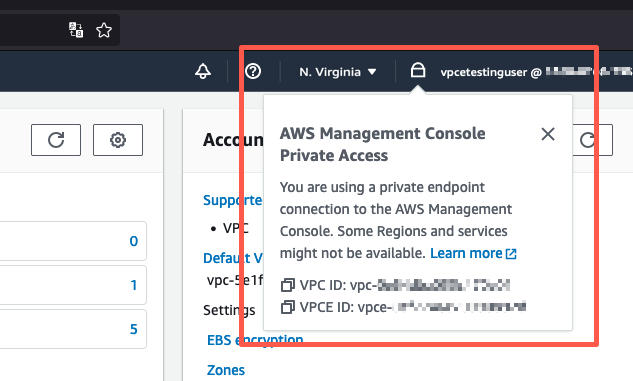
Selecione o ícone de cadeado na barra de navegação para ver o endpoint da VPC em uso. A captura de tela a seguir mostra a localização do ícone de cadeado e as informações da VPC.